In a digitally driven age, home internet security has never been more paramount. A 2020 study by Cybersecurity Ventures predicted that by 2025, cybercrime will cost the world $10.5 trillion annually. This alarming growth spotlights the necessity of fortified online defenses for personal users. As homeowners connect an increasing array of devices, understanding fundamental security practices ensures not just protection of personal data, but contributes to global digital safety.
Understanding Internet Security
Internet security, the sentinel of our digital lives, safeguards against a deluge of cyber threats. Beyond protection, it empowers us to navigate the virtual world with confidence, preserving privacy, data integrity, and peace of mind.
Common Types of Cyber Threats
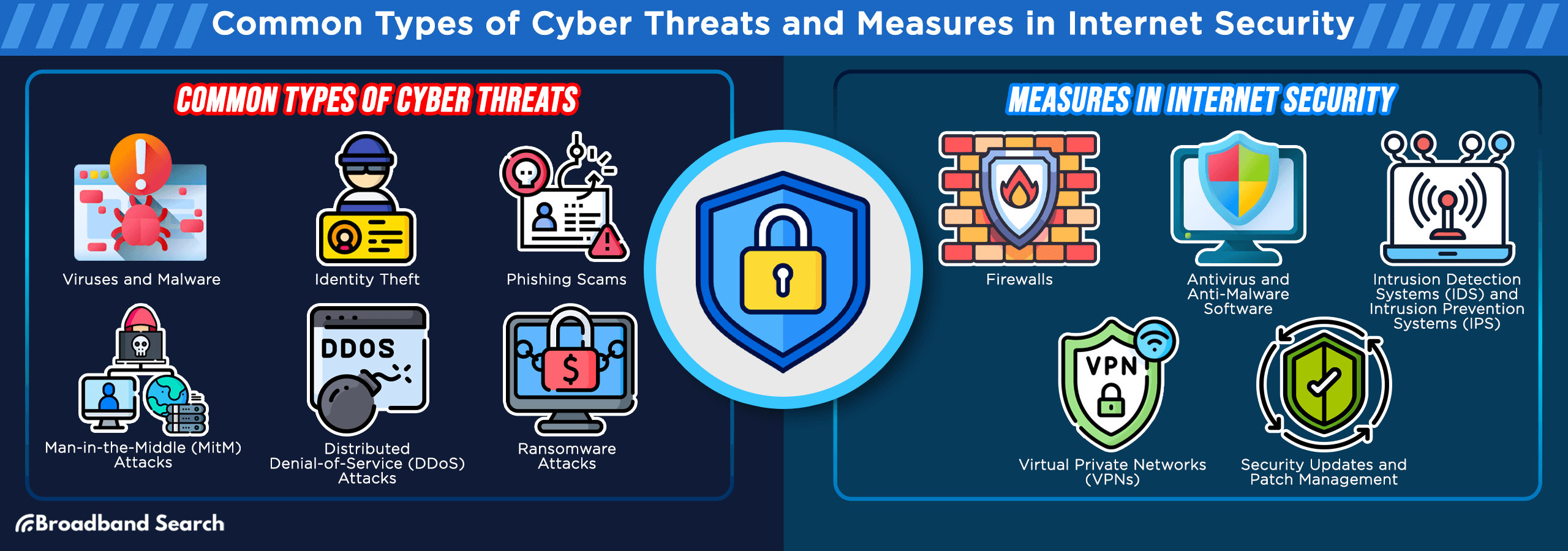
Viruses and malware
Viruses and malware are malicious software programs designed to infiltrate and compromise your devices. A recent study by cybersecurity experts revealed that over 560,000 new malware variants are detected daily, highlighting the escalating threat. These digital parasites can corrupt files, steal sensitive information, and even take control of your computer.
Identity theft
Identity theft is a pervasive cybercrime with far-reaching consequences. In the United States alone, the Federal Trade Commission reported a staggering 1.4 million cases of identity theft in 2021. Criminals use stolen personal information to commit financial fraud and engage in illicit activities, leaving victims to grapple with the aftermath.
Phishing scams
Phishing scams are cunning tactics employed by cybercriminals to deceive users into revealing confidential information. An alarming 97% of people worldwide cannot correctly identify a sophisticated phishing email. These scams can lead to financial losses, data breaches, and reputational damage.
Man-in-the-Middle (MitM) Attacks
MitM attacks involve intercepting and eavesdropping on communication between two parties. A recent Cofense Intelligence report highlighted a 35% increase in MitM between Q1 2022 and Q1 2023, underlining their growing prevalence. Attackers exploit vulnerable network connections to steal sensitive data or manipulate information.
Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks flood a target's server with a massive volume of traffic, rendering it inaccessible. In 2017, there was a notable surge in DDoS attacks, with a record-breaking 2.9 terabits per second attack reported. These attacks disrupt online services, causing financial losses and damaging reputations.
Ransomware attacks
Ransomware attacks are on the rise, with a 148% increase in 2021 as reported by SonicWall. These attacks encrypt a victim's data, holding it hostage until a ransom is paid. Victims often face difficult decisions, and even if they pay the ransom, there is no guarantee they will regain access to their data.
Entities and Measures in Internet Security
Firewalls
Firewalls serve as a critical defense mechanism, acting as a barrier between trusted networks and potentially harmful untrusted networks. Recent cybersecurity research indicates that firewalls are instrumental in reducing the risk of unauthorized access and thwarting potential threats. They meticulously analyze incoming and outgoing traffic, allowing only legitimate data to pass through while blocking malicious attempts.
Antivirus and Anti-Malware Software
Antivirus and anti-malware software play a pivotal role in safeguarding your devices. A recent study by AV-TEST, a leading independent antivirus testing organization, revealed that these software solutions effectively detect and remove 99.9% of malware threats. They continuously scan your system for malicious software, ensuring your digital environment remains secure.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS are cybersecurity sentinels that monitor network traffic for any hint of suspicious activity. They are invaluable in identifying potential threats before they escalate. Recent statistics show a surge in the sophistication of cyberattacks, emphasizing the need for robust intrusion detection and prevention mechanisms. IDS identifies anomalies, while IPS takes proactive steps to prevent intrusions, bolstering your network's security posture.
Virtual Private Networks (VPNs)
VPNs are essential tools for enhancing online privacy and security. They encrypt internet connections, rendering them impervious to prying eyes. In an era where public Wi-Fi usage is widespread, VPNs are becoming indispensable. Recent privacy breaches underscore the significance of VPNs in safeguarding sensitive data during online interactions. They provide anonymity and protect your digital footprint when accessing public networks.
Security Updates and Patch Management
Regularly updating operating systems, software, and firmware is a linchpin of internet security. Studies have shown that neglecting security updates can lead to vulnerabilities that cybercriminals exploit. Timely updates and efficient patch management fortify your defenses, ensuring that potential entry points for cyber threats are sealed, and your system remains resilient in the face of evolving risks.
Steps to Secure Your Home Internet
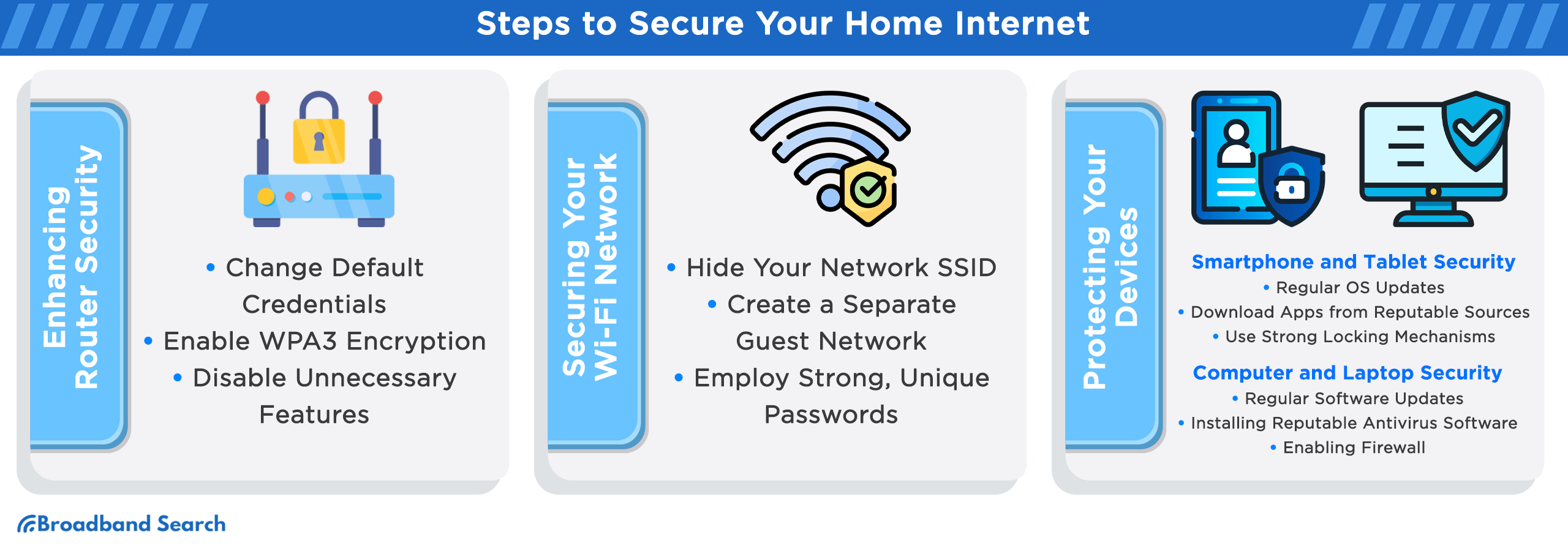
Enhancing Router Security
In an era where home internet usage is ubiquitous, safeguarding your router is paramount. Recent studies highlight the urgency of the matter, with router-related cyberattacks on the rise, accounting for 83% of all breaches. Follow these steps:
- Change Default Credentials: Replace default usernames and passwords with strong, unique credentials. Default login information is a common entry point for cybercriminals.
- Enable WPA3 Encryption: Upgrade to WPA3 encryption to secure your Wi-Fi network. WPA3 offers enhanced protection against brute-force attacks and improves overall security.
- Disable Unnecessary Features: Turn off unnecessary router features like remote management and WPS (Wi-Fi Protected Setup). These features can create vulnerabilities if left active.
By implementing these measures, you can bolster your home internet security and reduce the risk of falling victim to router-based cyber threats. It's a proactive step toward safeguarding your digital sanctuary.
Securing Your Wi-Fi Network
When it comes to internet security, your Wi-Fi network is the first line of defense. Implement these essential steps to secure it against potential threats:
- Hide Your Network SSID: By concealing your network's SSID (Service Set Identifier), you make it less visible to potential intruders. This added layer of obscurity can deter casual unauthorized access.
- Create a Separate Guest Network: Establish a separate network for guests with limited access privileges. This prevents them from reaching sensitive devices on your main network.
- Employ Strong, Unique Passwords: Craft robust and unique passwords for both your Wi-Fi network and router. Avoid easily guessable phrases, such as "password123." Recent study found that weak passwords are the primary entry point for cyberattacks. Utilize a combination of letters, numbers, and symbols for maximum security.
Protecting Your Devices
Smartphone and Tablet Security
Securing your mobile devices extends beyond convenience; it's a fundamental step in safeguarding your digital life from an array of evolving threats. By adopting these practices, you safeguard your smartphone and tablet against potential security breaches.
- Regular OS Updates:
Regularly updating your device's operating system ensures you have the latest security patches. Cybercriminals often exploit vulnerabilities in older OS versions.
- Download Apps from Reputable Sources:
Avoid third-party app stores and only download apps from official sources like Google Play or the Apple App Store. These platforms vet apps for potential threats.
- Use Strong Locking Mechanisms:
Utilize robust PINs, passwords, or biometric authentication methods like fingerprints or facial recognition. Weak or no lock mechanisms can lead to unauthorized access and data breaches.
Computer and Laptop Security
Safeguarding your computer and laptop is imperative in today's digital landscape. As gateways to our virtual lives, these devices demand meticulous security measures to ensure the integrity of our online presence.
- Regular Software Updates:
Frequent software updates are vital for maintaining computer security. A 2018 study found that 85% of security breaches result from unpatched vulnerabilities. Updates often include critical security patches that safeguard against emerging threats.
- Installing Reputable Antivirus Software:
Using reputable antivirus software is a cornerstone of computer security. It provides a crucial layer of defense against viruses, malware, and other malicious software.
- Enabling Firewall:
Firewalls act as a protective barrier between your computer and potential threats. They monitor incoming and outgoing network traffic, blocking unauthorized access. Cybersecurity experts suggest enabling firewalls to reduce the risk of cyberattacks and data breaches.
How to Enable Firewall on Windows 11
- Press the Start button.
- Choose Settings from the Start Menu.
- Once the Settings window is visible, navigate to Privacy & Security on the left-hand side.
- Click on Windows Security located on the right side.
- From the subsequent options on the right, pick Firewall & network protection.
- The Firewall & network protection section will be displayed. From there, opt for either Domain network, Private network, or Public network.
- Under the Microsoft Defender Firewall section, use the toggle switch to either activate or deactivate it.
How to Enable Firewall on Mac
- Click the Apple logo situated at the top-left corner of your screen.
- From the appearing menu, choose System Settings.
Alternative approach: If the System Settings icon is visible on the Dock, you can click it directly.
- Upon the System Settings panel display, find and click Network on the left side.
- Navigate to and choose Firewall on the right side.
- Use the toggle switch to turn the firewall On or Off.
Safe Online Behaviors
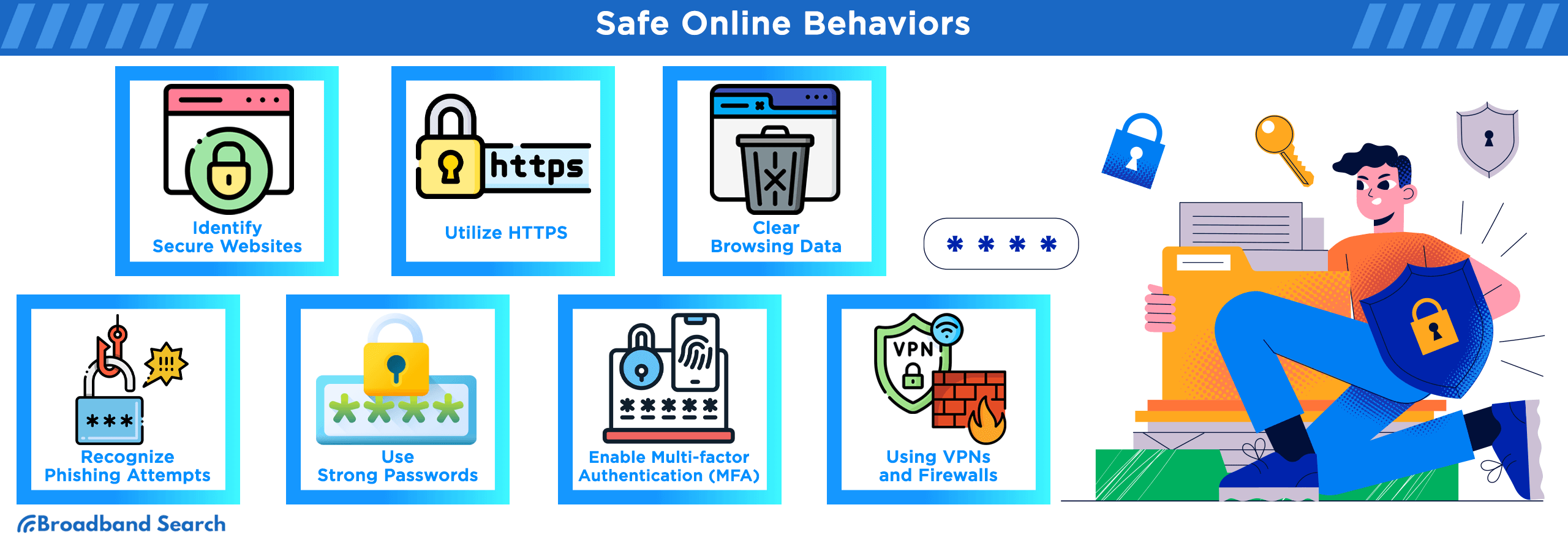
Browsing Safely
Adopting these safe online browsing practices enhances your internet security, protecting your personal data and ensuring a safer digital experience.
- Identifying Secure Websites:
Before sharing sensitive information, verify a website's legitimacy. Look for "https://" in the URL, a padlock icon, and scrutinize website addresses for typos or suspicious domains.
- Utilizing HTTPS:
Always prioritize websites with HTTPS over HTTP. HTTPS encrypts data exchanged between your device and the website, enhancing confidentiality and security.
- Clearing Browsing Data:
Periodically clear your browser's history, cookies, and cache to maintain privacy. Unwanted data accumulation can compromise your online security and reveal your browsing habits.
How to Clear the Cache and Cookies in Google Chrome:
- Launch Chrome.
- Go to ⋮ > More Tools > Clear browsing data.
- Choose your desired time range.
- Select Cookies and other site data and Cached images and files. Hit Clear data.
How to Clear the Cache and Cookies in Mozilla Firefox:
- Open Firefox.
- Go to ☰ > Settings.
- Choose Privacy & Security, find Cookies and Site Data, then hit Clear Data.
- Tick Cookies and Site Data and Cached Web Content. Press Clear.
- Confirm by clicking Clear Now.
How to Clear the Cache and Cookies in Microsoft Edge:
- Start Edge.
- Navigate to … > Settings.
- Click on Choose what to clear under Clear browsing data.
- Mark Cookies and saved website and Cached data and files. Press Clear.
Email Security
Email is a cornerstone of digital communication, but it's also a prime target for cyber threats. Ensuring the security of your email is essential, as it guards against phishing attempts, unauthorized access, and data breaches.
- Recognizing Phishing Attempts:
Phishing emails often masquerade as legitimate messages to steal sensitive information. Vigilance is key; scrutinize email sender addresses, avoid clicking on suspicious links, and never share personal or financial data via email.
- Using Strong and Unique Passwords:
Create robust, unique passwords for your email accounts. Password managers can help generate and store complex passwords, reducing the risk of unauthorized access.
- Enabling Multi-factor Authentication (MFA):
MFA adds an extra layer of security by requiring multiple forms of verification, such as a code sent to your phone. It enhances email security by making it significantly harder for unauthorized parties to access your account.
Using VPNs and Firewalls
Benefits and Uses
Both VPNs and firewalls play crucial roles in bolstering online privacy and security. VPNs ensure anonymity and data encryption, while firewalls provide network protection by filtering traffic. Together, they create a robust defense against the ever-evolving landscape of cyber threats, making them indispensable tools for the modern internet user.
VPN Functionality:
- VPNs, or Virtual Private Networks, create encrypted tunnels between your device and a server, concealing your online activities from prying eyes.
- They mask your IP address, enhancing anonymity and preventing third parties from tracking your online behavior.
- VPNs are vital when using public Wi-Fi, as they protect against data interception and cyberattacks on unsecured networks.
Firewall Functionality:
- Firewalls act as digital barriers, monitoring and controlling incoming and outgoing network traffic.
- They filter out malicious data packets, preventing unauthorized access to your network.
- Firewalls are essential for safeguarding against cyber threats like malware, phishing attacks, and intrusions.
Setting Up and Choosing the Right VPN and Firewall
Choosing the right VPN and optimizing your firewall are essential steps in enhancing your online security. By following these steps and considerations, you can effectively set up and select the right VPN and firewall solutions to bolster your online security and protect your home internet from potential threats.
Setting Up VPNs:
- Choose a reputable VPN service that aligns with your privacy needs and budget.
- Download and install the VPN client on your device.
- Follow the setup instructions, connect to a server in your preferred location.
- Enable the kill switch feature to halt internet access if the VPN connection drops.
- Regularly update the VPN client for security patches and improvements.
Setting Up Firewalls:
- Ensure your device's built-in firewall is enabled.
- Customize firewall settings to allow essential applications and block suspicious ones.
- Regularly update the firewall software to stay protected against emerging threats.
- Configure port forwarding for specific applications if needed.
- Monitor firewall logs for any unusual network activity.
Choosing the Right VPN and Firewall:
- Research VPN providers and read reviews to assess their reliability and privacy policies.
- Consider the number of servers and server locations offered by the VPN service.
- Evaluate the firewall's compatibility with your operating system and network requirements.
- Opt for VPNs and firewalls that offer customer support for assistance when needed.
- Balance cost with features to find the best combination for your internet security needs.
Implementing Advanced Security Measures
Two-Factor Authentication (2FA)
2FA is a cybersecurity method that adds an extra layer of protection to your accounts. It requires users to provide two separate forms of identification before granting access, typically something they know (like a password) and something they have (like a mobile device).
2FA is crucial because it significantly enhances account security. Even if someone manages to steal your password, they won't be able to access your account without the second factor, which is often a unique code generated in real-time.
TikTok
- Go to TikTok For Business User Settings > Security.
- Check the box for Text message.
- Enter the verification code sent to your phone; click Next. (Add a phone number if not already linked.)
- Confirmation: "2-step verification by text message activated."
Gmail
- Go to your Google Account.
- Click Security on the navigation panel.
- Under "Signing in to Google," choose 2-Step Verification > Get started.
- Follow the prompts.
Note: For work, school, or group accounts, contact your administrator if setup is unavailable.
- Access Security and login settings.
- Click Edit beside Use two-factor authentication.
- Pick a security method; follow instructions. Options are:
- Use a security key on a compatible device.
- Codes from a third-party authentication app.
- SMS codes from your phone.
- Go to More > Settings and privacy.
- Select Security and account access > Security.
- Choose Two-factor authentication.
- Pick from: Text message, Authentication app, or Security key.
- Click More > Settings at the bottom left.
- Select Privacy and Security on the left menu.
- Go to Two-factor authentication; click Edit.
- Choose a security method; follow on-screen instructions.
Regular Backups
Data loss can occur due to various reasons, including hardware failure, malware attacks, accidental deletions, or natural disasters. Without backups, recovering lost data can be a daunting and sometimes impossible task. Regular backups act as a safety net, providing peace of mind and the ability to restore critical information swiftly.
Effective Backup Strategies
- Automate Regular Backups: Use backup software or cloud services that offer automatic scheduling to ensure consistency.
- Multiple Copies: Maintain multiple copies of your data, including both local and offsite backups.
- Versioning: Opt for solutions that offer versioning, allowing you to recover earlier versions of files.
- Encryption: Ensure that your backups are encrypted to protect sensitive information.
- Test Restorations: Periodically test the restoration process to verify that your backups are functioning correctly.
Best Backup Services to Consider
- Cloud Backup Services: Providers like Dropbox, Google Drive, and iCloud offer secure cloud storage with easy-to-use backup options.
- External Hard Drives: Physical storage devices provide a tangible backup solution. Consider using both external hard drives and network-attached storage (NAS) for redundancy.
- Network Attached Storage (NAS): Ideal for home networks, NAS devices offer centralized storage with automated backup capabilities.
- Online Backup Services: Providers like Backblaze and Carbonite offer continuous, cloud-based backups with robust security.
Children and Internet Security
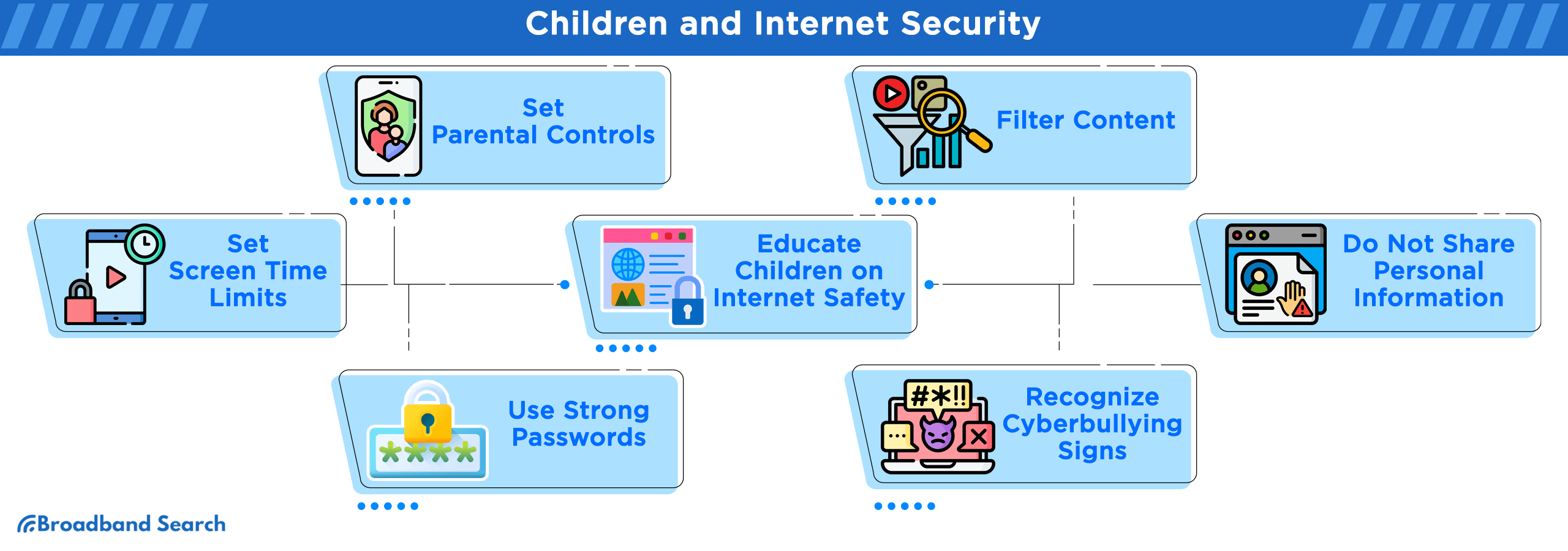
Setting Parental Controls
While the online world offers countless educational opportunities and entertainment, it also exposes children to various risks and inappropriate content. To strike a balance between the benefits and potential dangers, setting up parental controls is essential.
Filtering Content
Parental control features allow you to filter and restrict the content your children can access online. These filters typically categorize content based on its appropriateness for different age groups. For example, you can block access to explicit websites, violence, or mature themes. One highly regarded app for this purpose is Norton Family, which offers comprehensive content filtering options.
Setting Screen Time Limits
Excessive screen time can negatively impact a child's development, leading to various issues such as sleep disturbances and decreased physical activity. Parental control tools also enable you to set screen time limits, allowing you to manage the amount of time your child spends online. Apps like Qustodio provide flexible scheduling and time management features, allowing you to strike a healthy balance between online and offline activities.
Educating Children on Internet Safety
Educating children about the potential risks and fostering open communication is vital. For instance, parents can explain the importance of not sharing personal information with strangers online, using strong and unique passwords, and recognizing the signs of cyberbullying. By engaging in dialogue and providing guidance, parents empower their children to navigate the online world safely and seek help when faced with challenges.
Continuous Learning and Updating
Staying Informed About Latest Threats
Staying informed about the latest threats and developments is crucial. Cyber threats continue to surge, with a 400% increase in ransomware attacks reported in the past year. To navigate this digital minefield effectively, consider these resources and strategies:
- Security Blogs and Websites: Regularly visit trusted cybersecurity blogs and websites like KrebsOnSecurity and Threatpost for up-to-date information on emerging threats.
- Security Newsletters: Subscribe to newsletters from reputable cybersecurity organizations, such as the Cybersecurity and Infrastructure Security Agency (CISA), to receive timely updates and advisories.
- Online Forums and Communities: Participate in online forums and communities dedicated to cybersecurity, where experts and enthusiasts discuss emerging threats and share insights.
- Security Webinars and Conferences: Attend webinars and conferences conducted by cybersecurity experts to gain insights into the latest trends and vulnerabilities.
Regular Security Audits and Updates
Maintaining a safe and secure home internet requires more than just initial setup. Regular security audits and updates are crucial in an ever-evolving digital landscape. Here's why they matter and practical advice on how to conduct them:
- Device Firmware Updates: Keep your routers, modems, and IoT devices up to date to patch security vulnerabilities. An outdated router firmware may expose your network to potential threats.
- Software Updates: Regularly update your operating systems, applications, and antivirus software to patch vulnerabilities. Cybercriminals exploit outdated software.
- Password Audits: Change passwords periodically and ensure they are strong and unique. Password managers can help you keep track of them.
- Network Audits: Analyze your network traffic for anomalies using intrusion detection systems (IDS) and intrusion prevention systems (IPS). An unusual spike in network activity may indicate a cyber intrusion.
The Bottom Line
The journey towards safeguarding your home network and digital life is an ongoing one. We've explored various facets, from setting up firewalls to educating children on online safety. But it's crucial to recognize that the ever-evolving threat landscape demands continuous learning and vigilance.
The key takeaway is that your internet security posture should be as dynamic as the threats it seeks to mitigate. Cybercriminals constantly adapt, making it imperative for you to stay informed, update your defenses, and embrace best practices. By regularly auditing your security measures, staying informed about emerging threats, and educating yourself and your family, you can create a robust defense against the ever-present dangers of the digital world.
Remember, in the world of Internet security, complacency is the adversary. As technology advances and new vulnerabilities emerge, your commitment to securing your home internet remains paramount. Stay vigilant, stay informed, and maintain a strong security posture to ensure that your online experience remains safe, secure, and protected.
FAQ
How often should I change my passwords, and what makes a password strong?
It's recommended to change passwords every 3-6 months or immediately if you suspect a breach. A strong password typically contains at least 12 characters and includes a combination of upper and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays, names, or common words.
What are cookies, and why do websites use them?
Cookies are small files that websites store on your computer or device to remember information about you, like login status, preferences, or items in a shopping cart. Regularly clearing cookies can help protect your privacy and prevent websites from collecting extensive data on your browsing habits.
What is the difference between antivirus and anti-malware software?
While both software types are designed to combat malicious software, antivirus traditionally focuses on older, more established threats like viruses, worms, and Trojans. In contrast, anti-malware (also known as antimalware) tends to focus on newer threats such as zero-day exploits and ransomware.
Can my smart home devices (like thermostats or voice assistants) be a security risk?
Yes, any device connected to the internet can pose a potential security risk. Many smart devices have been targeted in the past due to lax security protocols. It's essential to regularly update their firmware, change default credentials, and ensure they are on a secure network, possibly even a separate network from your primary devices.
Why should I be cautious about public Wi-Fi networks, and how can I use them safely?
If you need to use a public network, avoid accessing sensitive sites (like online banking), and always ensure you're connecting to the legitimate Wi-Fi provided (and not a rogue hotspot). Using a VPN while on public Wi-Fi can also encrypt your data, making it harder for eavesdroppers to decipher.