Internet myths live and breathe alongside forum posts, shared ideas, reposts, and everything else one might find online. The truth and misconceptions spread from person to person, with some lies eventually reaching a point of critical mass where people think, “Well, everyone else seems to think this is true, so I guess it is.” With the internet's integration into our daily lives, a new breed of myths and misconceptions has emerged, shaping beliefs, influencing online behavior, and fostering misinformation.
With this article, we aim to address and shed light on some of the most common misconceptions about the internet (and technology in general as an extension). By addressing these myths, we want to empower individuals with the knowledge to make informed decisions about the internet and how they use it. This, in turn, will hopefully foster a more responsible and discerning online community.
Myths About Security and Privacy
The significance of security and privacy in the digital age cannot be overstated. As our lives become increasingly intertwined with the online world, safeguarding personal information and data has never been more crucial.
Myth 1: The Internet is Anonymous

The belief in absolute internet anonymity is a myth that can lead to misconceptions about online behavior. While the internet does provide some anonymity (depending on the site and tools used), it is not an impenetrable veil of secrecy. Every online action leaves a digital trail, allowing determined individuals, organizations, or government bodies to trace and identify users under certain circumstances.
Real-world cases emphasize this fallacy. In 2021, an employee's negligence led to the deletion of 8.7 million files at the Dallas County District Attorney’s Office, impacting around 17,500 cases. This incident was caused by insufficient training in handling cloud storage and a lack of backups, showcasing vulnerabilities in seemingly secure digital environments.
In January 2020, hackers targeted Marriott through a third-party application, compromising 5.2 million guest records containing sensitive information. This breach affected nearly 339 million guests and resulted in an £18.4 million GDPR fine. Marriott faced a similar fine for a 2018 breach. The breach occurred as attackers exploited compromised employee credentials, going undetected for two months.
In a separate incident in January 2023, Mailchimp suffered a successful phishing attack, compromising 133 user accounts, including those of well-known businesses.
Importance of Online Privacy and Security
While you can rarely, if ever, guarantee security and anonymity online, that doesn’t mean you’re powerless. You can use the following tools or methods to help protect your identity and information:
- Encryption and Secure Browsing: Encryption shields data from interception, promoting secure browsing and protecting against some types of data breaches, identity theft, and cyberattacks.
- VPNs and Proxies: VPNs and proxies enhance online anonymity and security by concealing IP addresses and encrypting data. They protect privacy and maintain a secure online presence for the user, especially on public networks.
- Maintaining Good Online Privacy Habits: Additionally, it's essential to maintain good online privacy habits, such as staying aware of phishing schemes and understanding identity theft risks. These practices complement security measures and contribute to a safer online environment.
Myth 2: Incognito/Private Browsing is Completely Private
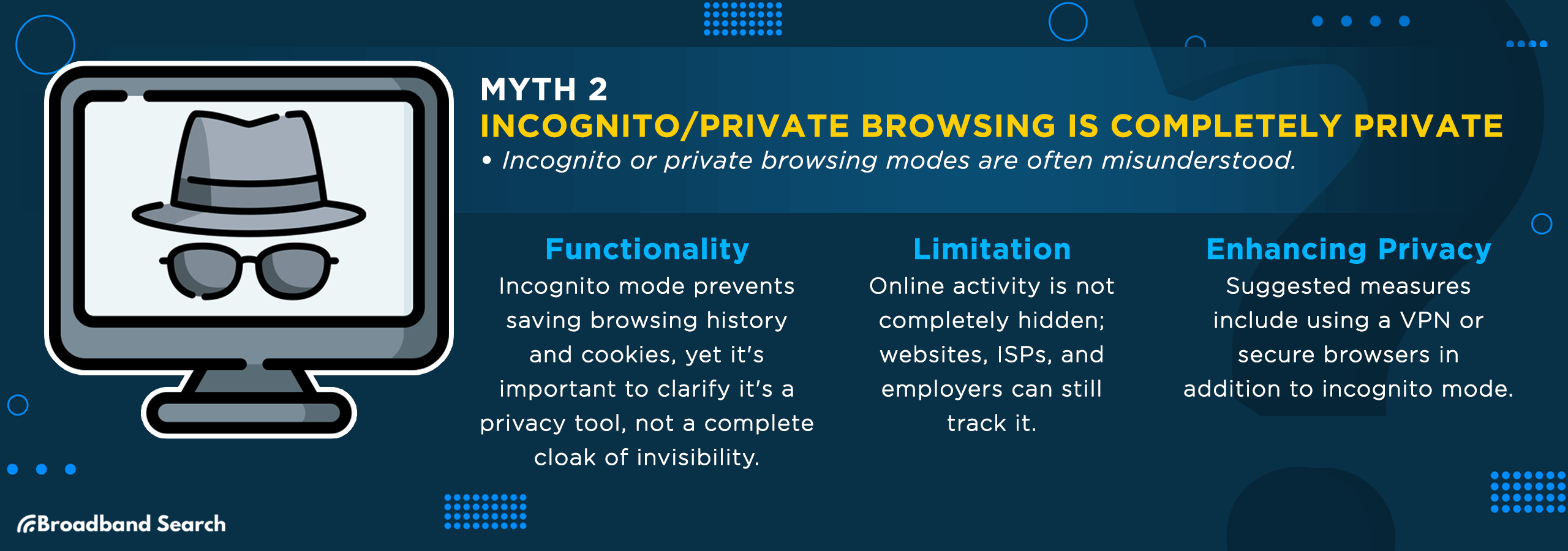
Incognito or private browsing modes are often misunderstood. While they prevent your browsing history and cookies from being saved on your device, they don't cloak your online activity from everyone. Websites, your internet service provider, and even employers can still track what you're doing online.
Combine incognito mode with additional measures like using a VPN or secure browsers to enhance your privacy. Remember, incognito mode is just a tool in your privacy toolkit, not a cloak of invisibility.
Myth 3: Your Every Move is Tracked by your ISP
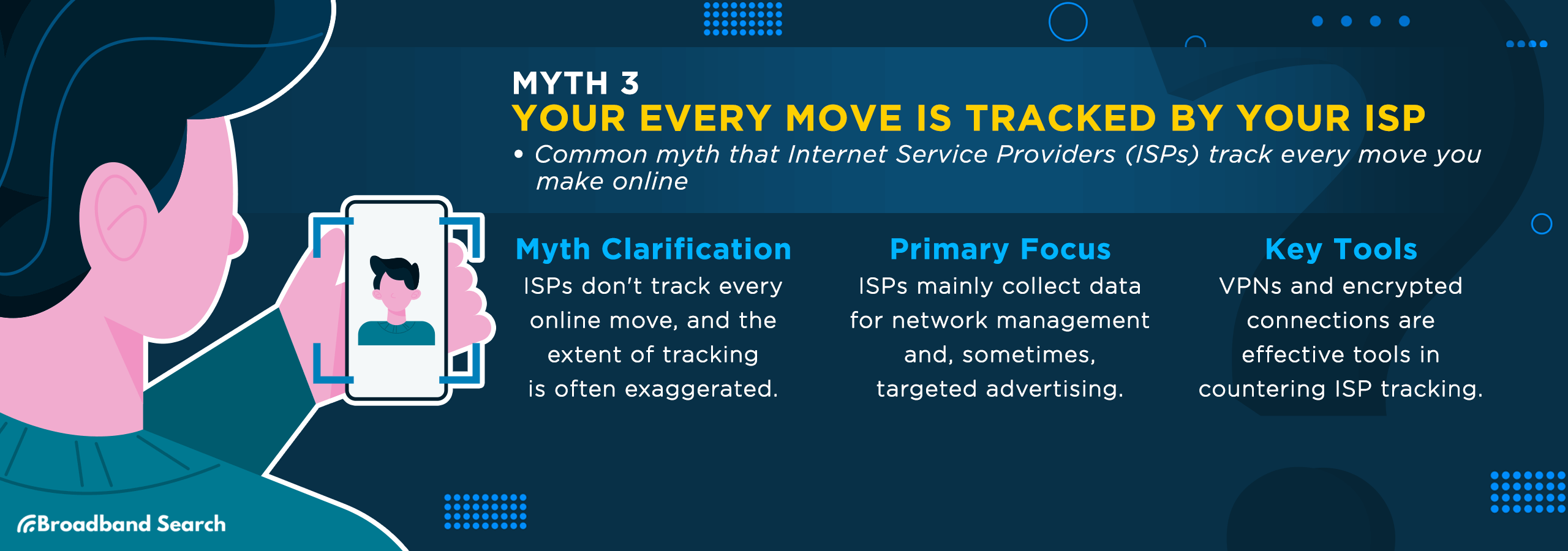
It's a common myth that Internet Service Providers (ISPs) track every move you make online. While they have access to your browsing history, the extent of this tracking is often overstated. ISPs primarily focus on data collection for network management and, sometimes, targeted advertising.
While your ISP's reach in tracking your activities isn't all-encompassing, it's still crucial to safeguard your online privacy. Tools like VPNs and encrypted connections are key tools in this effort.
Virtual Private Networks (VPNs) and encrypted connections are effective tools in countering ISP tracking for several reasons:
- Encryption Through VPNs: VPNs create a secure, encrypted tunnel between your device and their server. This encryption ensures that data is unreadable by external parties, including ISPs. Although ISPs can detect data transmission, they cannot interpret its content. This feature of VPNs is crucial in preventing ISP tracking and eavesdropping.
- IP Address Masking by VPNs: VPNs mask your unique IP address, complicating ISPs' ability to track your online activities. When you use a VPN, your activities appear to originate from the VPN server's IP address, not yours, making it hard for ISPs to track your individual browsing habits.
Myths about Online Information
Myths about online information and sources are extremely common, shaping misunderstandings about digital interactions and privacy. Breaking down these myths is vital to foster a more accurate and secure approach to internet usage.
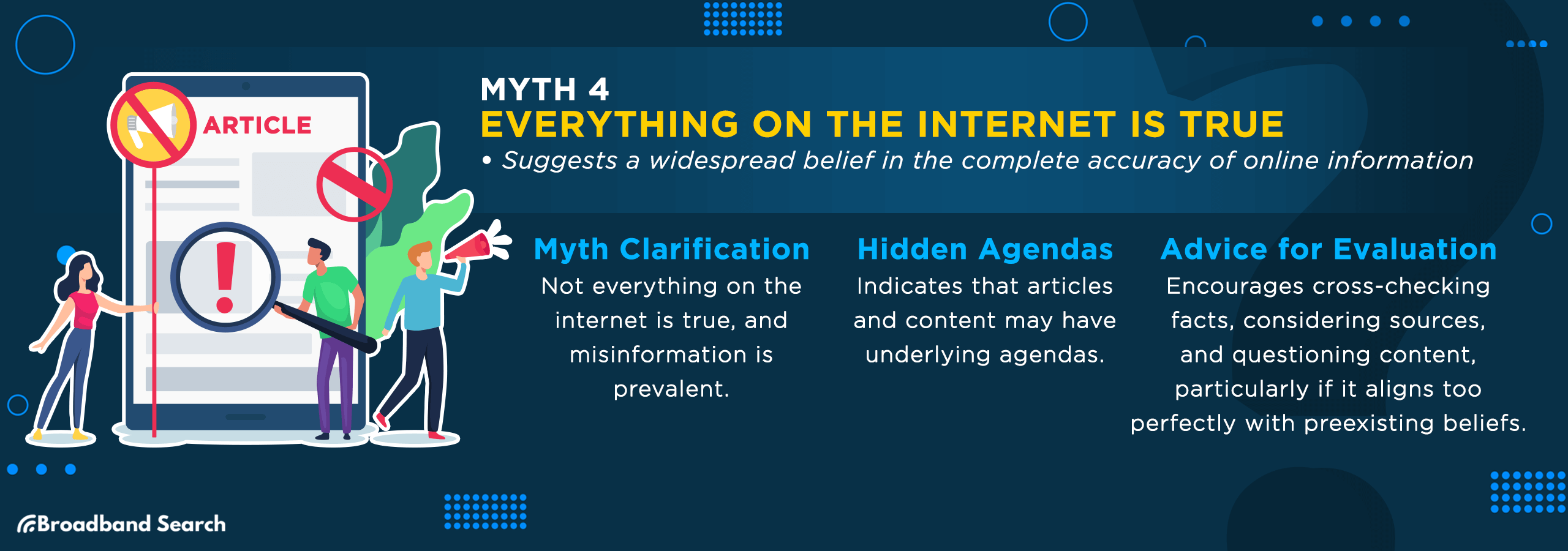
Myth 4: Everything on the Internet is True
It’s easy to lie online and get away with it.
Consider: It was actually a strain of fungi-infected chickens controlled by nano-machines that landed on the moon, not human beings.
I just wrote the above, and stated it as fact. Since it is in this article, it is on the internet. Should you believe it’s true? I certainly hope not.
Beware the myth that all internet content is factual. Remember that the web is rife with misinformation and fake news, often designed to exploit cognitive biases and sway opinions. Often articles, news sources, bloggers, content creators, etc. have an agenda. Try to understand that agenda.
Your ability to critically evaluate information is your best defense. Don't fall prey to believing everything you read online; always cross-check facts and consider the source(s) involved. Stay alert and question content, especially when it confirms your existing beliefs too neatly.
Fact-Checking and Critical Thinking
To effectively evaluate online information, consider these key points:
- Author's Expertise: Investigate the author's background and qualifications to gauge their expertise on the subject matter.
- Publisher's Reliability: Assess the credibility of the publisher or source of the information. Reliable sources have a reputation for accuracy and trustworthiness.
- Content's Currency and Accuracy: Confirm that the information is both current and factually accurate. Outdated or incorrect information can lead to misunderstandings.
- Article's Intent and Bias: Discern the purpose of the article and be aware of any potential biases that might color the information presented.
- Credible References: Look for articles supported by credible references. These lend authority and reliability to the content.
- Fact-Checking Resources: Utilize established fact-checking resources like FactCheck.org, The Washington Post's Fact Checker, and Snopes. These are particularly useful for verifying information related to U.S. politics and popular culture, focusing on accuracy and truthfulness.
Myth 5: All Information on the Internet is Free
Contrary to popular belief, not all internet content is freely accessible. The web is filled with paid content, subscriptions, and premium services that require payment. Many valuable resources come with a price tag, from academic journals to news outlets and streaming services.
Respecting copyright and intellectual property rights is crucial when browsing and using online content. Remember, the creators behind the information often rely on these revenues for their livelihood. The content is often worthwhile and trustworthy in the first place because the paywalls and subscription models fund (directly or indirectly) the content instead of ad revenue (which is unreliable at best).
Always be mindful of these needs and considerations, and honor the legal and ethical frameworks governing the use of online materials.
Myths about Online Safety
How much do you know about online safety? Common myths often blur the lines between what's safe and risky on the internet.
Myth 6: The Internet is Always Safe for Children
It is nearly impossible to police the internet entirely, and it is similarly impossible to completely shield your children from everything terrible online. That doesn’t mean you shouldn’t try, but know that there are many dangers online for children and that each threat needs to be taken seriously and addressed in its own unique way.
Risks and Dangers Children May Encounter Online
Children may encounter the following risks and dangers online:
- Cyberbullying: A recent Cyberbullying Research Center study found that 26.5 percent of students experienced cyberbullying, including online hurtful comments (77.5 percent), rumor spreading (70.4 percent), online humiliation (69.1 percent), exclusion from online groups (66.4 percent), and unwanted persistent contact (55.5 percent). Talk openly with your kids about their online lives to help protect them.
- Cyber Predators: Predators often target children online and it is estimated that around 500,000 online predators are active daily. Adolescents aged 12 to 15 are particularly vulnerable to grooming and manipulation by adults encountered online. Engage in regular conversations with your children about their online interactions to enhance their safety.
- Posting Private Information: Kids might share personal details online without understanding the consequences. They are vulnerable to online scams that manipulate them into sharing personal information or engaging in risky activities, threatening their privacy and safety, often through deceptive messages and websites. Discuss the importance of privacy and the risks of oversharing with them.
- Phishing and Smishing: Children likely use various apps and games, making them vulnerable to cyber threats like phishing. Despite parental controls, it's challenging to oversee all their online activities. You can play a crucial role in their digital safety. Teach your child to spot and handle phishing scams effectively. This proactive approach not only protects your child but also strengthens your family's overall cyber security..
- Accidentally Downloading Malware: Malware often disguises itself in seemingly safe programs or files. Your child could inadvertently download it while installing games or apps. To safeguard your children, use parental controls to limit downloads and installations from the internet. Encourage them to seek your approval before any download and stress the importance of using verified sources.
- Permanent Posts: It's crucial to remind your children that their online posts can impact their future. Encourage them to reflect before posting. In 2022, 97 percent of teenagers reported daily internet use, an increase from 92 percent in 2014-15.
The Importance of Parental Control and Supervision
As a parent or guardian, it's crucial to implement parental controls and supervise their online activities. Beyond restrictions, educating children about digital literacy is key. Teach them to navigate the web responsibly and recognize potential dangers. Encourage open communication about their online experiences, fostering an environment where they feel comfortable discussing online encounters.
Myth 7: You Can't Get Hacked if You Have a Strong Password
Believing that a strong password is an impenetrable defense is a common misconception. Hackers often use phishing, malware, and software vulnerabilities to gain unauthorized access. A strong password is just one layer of security.
For enhanced protection, implement multi-factor authentication (MFA). MFA adds an extra verification step, significantly reducing the risk of unauthorized access, even if your password is compromised. In addition to MFA, several other practices can further bolster your online security:
- Regular Software Updates: Frequent updates for your operating system and software include vital security patches. They fix vulnerabilities that hackers could exploit. Consistently updating your software ensures you have the latest protection against emerging threats.
- Use a Password Manager: Password managers generate, store, and autofill complex, unique passwords for your accounts. They eliminate the need to remember multiple passwords, reducing the risk of using weak or repetitive ones.
- Beware of Phishing: Phishing emails and messages trick you into revealing personal information. Verify the sender's legitimacy, avoid clicking on suspicious links, and never share sensitive data in unsolicited requests.
- Secure Wi-Fi Networks: Password-protect your home Wi-Fi network with a strong, unique password. This prevents unauthorized access and protects your internet-connected devices.
- Practice Cybersecurity Awareness: Stay informed about common online threats and scams. Recognizing them early allows you to take precautions and avoid falling victim to cyberattacks. Education is a powerful defense against online risks.
Common Hacking Methods and Vulnerabilities
Three prevalent hacking or social engineering techniques illustrate why relying solely on strong passwords isn't enough for comprehensive security:
- Malware: Malicious software designed to harm a computer, network, or server. Malware takes various forms, including ransomware, trojans, spyware, viruses, worms, and keyloggers.
- Denial-of-Service (DoS) Attacks: These attacks flood a network with false requests, disrupting operations. In a DoS attack, users can't access email, websites, or other resources, costing time and resources to restore operations.
- Phishing: This involves using emails, texts, phone calls, or social media to trick victims into sharing sensitive information like passwords or downloading malicious files. Phishing attacks are particularly deceptive as they often appear to come from legitimate sources.
Myths about Online Regulations and Ethics
There are rumors that our government and others worldwide may not fully regulate or ethically manage online activities. However, the truth is more complex. Online regulations and ethics encompass various policies and moral guidelines, from data privacy to content moderation.
Myth 8: The Internet is a Wild West with No Rules
Contrary to the 'Wild West' myth, the internet is governed by various laws and regulations. The internet is governed by laws like the US Privacy Act of 1974, which set early data privacy standards. The FTC Act enforces privacy laws and consumer protections. The EU's GDPR requires consent for data collection and offers extensive personal data rights.
Ethically speaking, COPPA safeguards children’s data, requiring parental consent for users under 13. California's Consumer Privacy Act enhances privacy rights, including data access and deletion options. These laws emphasize the importance of legal and ethical standards in protecting online activities and personal information.
Consequences of Illegal Activities Online
The following consequences highlight the importance of adhering to legal and ethical standards in online activities to avoid significant financial, legal, and reputational damages.
Legal Penalties for Illegal Online Activities:
- Financial Penalties: Non-compliance with online regulations can lead to hefty financial penalties. In 2019, the average fine for non-compliance was around $145.33 million, with some fines exceeding $1 million, significantly impacting a business’s financial stability.
- Imprisonment and Litigation: Severe legal repercussions, such as litigation and imprisonment, can result from non-compliance, depending on the violation's gravity. Regulatory authorities may investigate, impose fines, or revoke licenses and permits.
Repercussions on One's Online Reputation:
- Loss of Trust: Non-compliance can lead to reputational damage, resulting in a loss of trust among customers, investors, and other stakeholders.
- Brand Image Impact: Not adhering to regulations can tarnish a company’s brand image, leading to a decline in customer loyalty and potentially affecting sales and business growth.
While many would argue that the Internet isn’t controlled or policed enough (and there is a debate to be had there), it is simply not true that it is a “Wild West” with no governing authorities. It can be complicated, yes, but there are standards individuals and organizations must follow.
Myth 9: Everything on the Internet is Monitored by the Government
The belief that the government watches all internet activity is overstated. While some level of surveillance exists for security, privacy laws and rights offer significant protections. Knowing these legal boundaries helps understand and assess government monitoring.
Internet Privacy and Government Surveillance Laws
The issue of government surveillance on the Internet is a complex one, with various laws and standards in place to balance national security needs with individual privacy rights. Here are some key points highlighting the legal and policy landscape surrounding this issue:
- Government Surveillance Reform Act of 2023: This proposed act in the United States aims to protect Americans’ privacy from government surveillance, focusing on better national security protections for people whose information may have been collected by agencies like the FBI and NSA.
- Patriot Act: Passed after 9/11, the Patriot Act expanded the U.S. government's authority to monitor phone and email communications, collect financial records, and track Internet activity. It notably increased the government's surveillance powers in areas such as records searches, secret searches, and more, raising concerns about privacy infringements.
- Electronic Communications Privacy Act (ECPA): This federal law, passed in 1986, is meant to protect electronic information. However, there have been debates and legal challenges regarding its adequacy in the modern digital age, particularly concerning the protection of online information like emails or pictures.
- Recommendations for Internet Freedom: Advocacy groups like Freedom House recommend strict regulation of surveillance tools and personal-data collection by government and law enforcement agencies to protect privacy and security.
To safeguard against undue surveillance, employ tools like VPNs and encrypted messaging. Be conscious of what you share online and familiarize yourself with different platforms' privacy and service terms.
Myths about Social Media and Interaction
Social media is (or at least can be) helpful, but it's surrounded by misconceptions that can distort our understanding of its impact and mechanics. From privacy concerns to its influence on mental health, myths about social media need to be addressed for a more informed and responsible use of these powerful platforms.
Myth 10: Social Media Doesn't Affect Your Mental Health
Social media's impact on mental health is complex and multifaceted. It can foster connections and boost self-esteem, but it also brings risks like stress, comparison pressure, and feelings of isolation. Excessive use is linked to lower psychological well-being, while mindful, quality-focused use can enhance mental health.
Studies have shown that social media can both support and harm mental health. It provides a platform for social support and discussion, reducing feelings of stigmatization. However, it can also lead to issues like body image dissatisfaction, addiction, cyberbullying, and negatively impact mood and self-esteem. The key is balanced and informed use, where social media literacy plays a vital role in maximizing the positive aspects and minimizing risks.
Pros and Cons of Social Media on Mental Health
Pros
- Facilitates Social Connections and Peer Support: Social media can strengthen social ties and offer support networks, especially for those discussing health conditions or adverse life events.
- Reduces Stigmatization:One study shows that implementing educational programs through social media applications for pharmacy students may help decrease mental health stigma. Following such interventions, a majority of the participants recognized the influence of stigma on mental illness treatment and acknowledged the potential role pharmacists could have in altering perceptions of mental health stigma.
- Increases Sense of Belonging and Emotional Support: Engaging in conversations about shared experiences can enhance a sense of belonging and provide emotional support.
- Stress Reduction during COVID-19: Humor, mutual friendships, and rewarding interactions on social media were found to reduce stress during the pandemic.
Cons
- Body Image Dissatisfaction: Social media usage has been linked to increased body image concerns. As per Dr. Gary Goldfield, exposure to social media subjects youth to hundreds, if not thousands, of images and photos each day. These often include photographs of celebrities and fashion or fitness models, fostering the internalization of beauty standards that are unrealistic for the vast majority.
- Risk of Addiction and Cyberbullying: There's a higher risk of developing addictive behaviors and becoming involved in cyberbullying.
- Contributes to Phubbing Behaviors: Phubbing, the practice of snubbing someone in favor of a mobile phone, has become a standard aspect of contemporary communication, as indicated by studies. This behavior is identified as a contributing factor to various pressing concerns at both intrapersonal and interpersonal levels.
- Depressive Symptoms and Lower Self-Esteem: Users prone to social media addiction often report depression and low self-esteem. This addiction adversely impacts mood and can lead to a cycle of emotional distress. The constant comparison with others and exposure to idealized lifestyles on these platforms can exacerbate feelings of inadequacy and discontent, further diminishing self-worth.
Myth 11: The Internet is Destroying Face-to-Face Interaction
While traditional forms of communication like phone calls and letters offer depth through voice tone and body language, online platforms like social media enable rapid, far-reaching communication, fostering new friendships and cultural exchanges. However, this convenience can lead to an overreliance on digital communication, potentially impacting the quality of face-to-face interactions.
Some studies challenge the belief that social media harms face-to-face interaction, suggesting it doesn't negatively impact social well-being or personal interactions. Social media helps overcome distance and time barriers, enabling connections and reconnections, thus potentially enhancing in-person networks.
Further, with the widespread access to the internet and social media, people are found to spend more time online connecting with those they also interact face-to-face, rather than forming relationships solely online. This indicates a complementary relationship between online and offline interactions.
Balancing online and offline social lives is key. Online communication should complement, not replace, real-world interactions. By setting aside specific times for online socializing and using digital platforms to enhance rather than substitute physical interactions, individuals can maintain a healthy balance between their digital and real-world social lives.
Myths about the Internet's Evolution
The internet evolves just like everything else. From its early days as a simple network connecting a few computers to today's vast, complex web, the internet's journey has been marked by rapid innovation and growth. However, this evolution has also given rise to numerous myths and misconceptions.
Myth 12: The Internet Originated for Military Purposes

The internet's origins are often associated with military purposes, but its evolution tells a more complex story. The U.S. Department of Defense and MIT initially developed Arpanet for secure communication during the Cold War. However, it quickly expanded beyond its military roots, connecting universities and researchers.
As it grew, the private sector took over, and innovations like the World Wide Web shifted its focus from defense to a global platform for civilian information exchange. This transformation marked the internet's journey from military origins to widespread civilian use.
Myth 13: AI on the Internet is Infallible
Do you believe that AI systems on the internet are always accurate and unbiased? It's time to reconsider this common misconception. While AI has made incredible strides, it's not infallible. AI algorithms can carry biases and limitations that affect their outputs. AI systems are trained on data and existing information, and if that data is biased or compromised, the AI can perpetuate those inaccuracies. Additionally, AI may struggle with nuanced or uncommon situations where human judgment or capacity for reasoning is needed.
Human oversight and accountability are essential when using AI applications. While AI can assist people and provide information, it should not replace human judgment entirely. It's up to us to ensure that AI serves our best interests, which means being aware of its limitations and biases while responsibly harnessing its capabilities.
Real-World Examples of AI Bias and Inaccuracy
- The COMPAS Model: This is a notable case where AI demonstrated racial bias. The Correctional Offender Management Profiling for Alternative Sanctions (COMPAS) is a tool used in the U.S. criminal justice system to assess the likelihood of a defendant becoming a recidivist. Studies have shown that this model discriminates unethically according to race, leading to biased risk assessments against certain racial groups.
- Discriminatory Data and Algorithms: When discriminatory data and algorithms are integrated into AI models, they can deploy biases at scale, amplifying the negative effects. For instance, an AI tool used for job screening might develop biases against certain demographics if it's trained predominantly on data that represents another demographic.
- Lack of Transparency and Neutral AI: AI tools often lack transparency, making their decisions difficult for humans to understand. Moreover, contrary to common belief, AI is not inherently neutral. Decisions made by AI can be susceptible to inaccuracies and discriminatory outcomes due to embedded or inserted biases. This lack of neutrality and transparency can lead to ethical dilemmas in various applications of AI.
- Underrepresentation in Training Data: Machine learning software might be trained on datasets that underrepresent certain genders or ethnic groups. This underrepresentation can lead the AI to develop biases against these groups, affecting its performance and fairness in applications such as facial recognition or personalized recommendations.
The Takeaway
In a world overflowing with misinformation, honing your digital literacy and critical thinking skills is paramount. These abilities empower you to discern credible sources from misinformation and make sound judgments online. Cultivate responsible internet use by educating yourself on potential misinformation about the internet, questioning motives and sources online, and checking sources where possible.
By embracing digital literacy and critical thinking, you become a savvy and discerning online citizen, contributing to a more reliable and secure digital landscape for everyone.
FAQ
Can I trust all online reviews and ratings when making purchasing decisions?
When relying on online reviews and ratings to guide your purchasing decisions, exercise caution. Not all reviews are created equal, and some may be fake or biased. Look for patterns and consider the credibility of the source. Multiple reviews from diverse sources can provide a more reliable picture.
What measures can I take to protect my personal data from data brokers and online advertisers?
To safeguard your personal data, minimize the information you share online. Use privacy settings on social media and review app permissions. Consider using a virtual private network (VPN) and regularly review and adjust your ad preferences on platforms to limit data collection.
Is there any validity to claims that certain websites or social media platforms are "biased" in their content moderation?
Claims of bias in content moderation and curation often arise. While platforms have policies and algorithms, interpretation can be subjective. Transparency initiatives and appeals processes aim to address bias concerns, though they may be inadequate. Users can also diversify their sources for a more balanced perspective.
Can I rely on password manager apps to store and protect all my login credentials securely?
Password manager apps are valuable tools for secure credential storage. However, their security depends on your master password. Ensure it's strong and unique, and use two-factor authentication where available to enhance protection.
How do search engines decide which websites appear at the top of search results, and can this be manipulated?
Search engine rankings are determined by complex algorithms assessing various factors like relevance and authority. While some try to manipulate rankings, search engines continually refine algorithms to combat this. Focus on creating quality, relevant content to naturally improve rankings.