Wi-Fi, for many, is as essential as electricity in modern homes and businesses. It powers our digital devices, keeps us connected, and drives the engine of our online world. However, like any resource, it's susceptible to misuse and theft. According to Kaspersky Security Network, nearly 25% of residential Wi-Fi networks remain unsecured, making them easy targets for unauthorized users. Ensuring your Wi-Fi is protected not only preserves bandwidth but guards against potential security breaches, making vigilance a necessity in today's interconnected landscape.
Signs of Unauthorized Wi-Fi Use
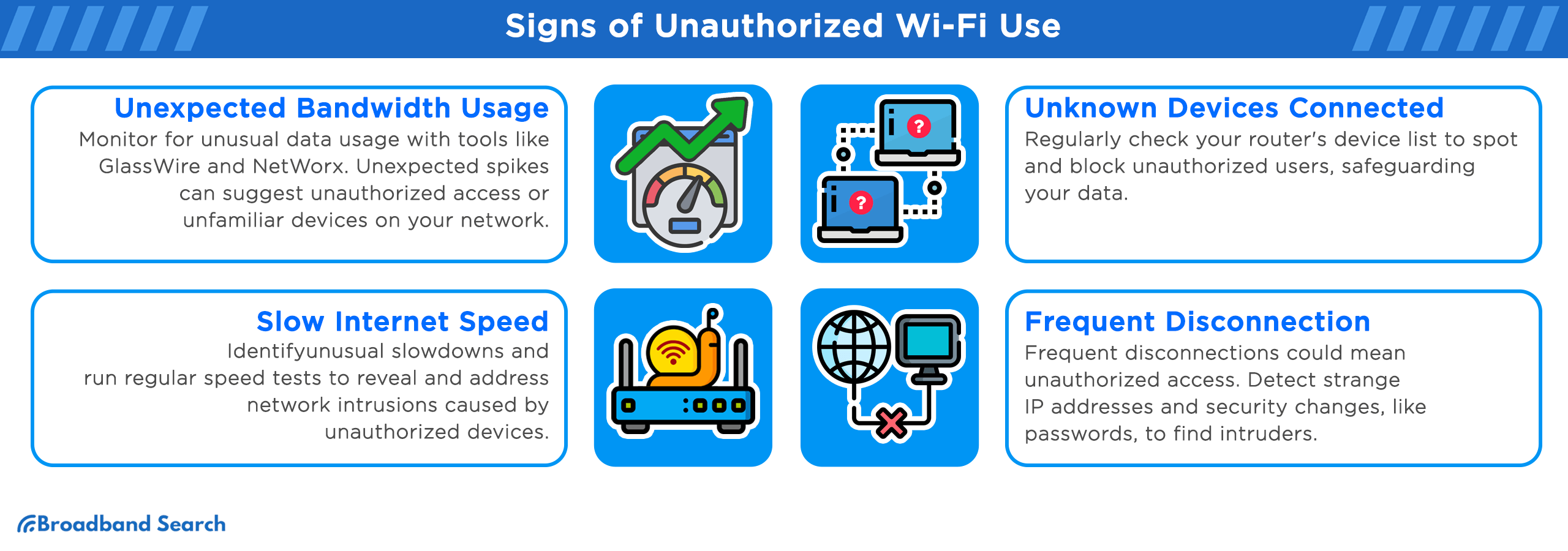
Unexpected Bandwidth Usage
Identifying unusual bandwidth consumption not only safeguards your Wi-Fi network from unauthorized access but also ensures optimal performance for legitimate, prioritized connections and activities.
- Monitoring Data Usage: Effective bandwidth management requires distinguishing between typical and abnormal data consumption. Tools like GlassWire or NetWorx provide real-time monitoring, flagging unexpected spikes in usage. One study highlighted that households, unaware of breaches, often experience a 74% surge in data use. Imagine streaming a movie only to face buffering; such interruptions could be clues of unauthorized Wi-Fi access.
- Identifying Unusual Activity: Significant data spikes during off-hours or unknown devices using vast amounts are red flags. A recent study found that Wi-Fi users have encountered unfamiliar devices on their networks. For instance, a home user might notice heavy data consumption at 2 AM, pointing to a potential breach.
Slow Internet Speed
Slow internet speeds can be more than just an inconvenience; they can be telltale signs of unauthorized Wi-Fi usage. By comprehending speed fluctuations and consistently running tests using platforms, users can diagnose and address unsolicited network intrusions.
- Understanding Speed Fluctuations: Normal variations in internet speed occur due to peak usage times or minor technical glitches. Suspicious slowdowns, often persistent, hint at unauthorized devices tethering your connection. For instance, households notice severe speed declines when unknown devices perform data-intensive tasks, negatively impacting the connection.
- Running Speed Tests: Scheduling regular speed tests helps monitor and maintain network health. BroadbandSearch Speed Test offers real-time speed analysis, helping identify discrepancies between expected and actual performance. In a case, a user discovered recurrent, unexplained speed dips, later traced back to unauthorized connections through vigilant testing.
Unknown Devices Connected
When unfamiliar devices silently leech off your Wi-Fi, the integrity of your network is compromised. By diligently inspecting your router's device list and discerning between recognized and unfamiliar device names, you can swiftly identify and thwart these unauthorized digital intruders.
- Checking Router’s Device List: Most routers present a list of gadgets that are currently or have recently accessed the network. Unfamiliar devices, if discovered, often indicate a security breach, necessitating immediate action to revoke access, secure your network, and protect sensitive data from potential exposure and misuse. Regularly scrutinizing this list aids in maintaining a secure, uncompromised connection.
Using Your Wireless Router
- Open a browser and log in to your router's web interface for network setup and user monitoring.
- Enter your router’s IP address in the address bar. Find the specific IP in the manual or manufacturer's web page; common ones include 192.168.1.1 and 10.0.0.1. Use Command Prompt on Windows (type CMD in Start, then type ipconfig /all and press Enter) to find the “Default Gateway” IP.
- Input your router's username and password. For default credentials, check the manual or manufacturer's web page. Typically, it's “admin” for both fields.
- Locate a list of connected devices in the interface, under various possible headings like "Connected Devices". This displays the device name and MAC address. Change your Wi-Fi password and use WPA2-PSK encryption if unknown devices are detected.
Using Command Prompt
- Open Command Prompt on Windows (press Windows key, type CMD) or Terminal on Mac (search for it using the magnifying glass icon).
- Type "arp -a".
- Review the IP addresses that share the same prefix as your router's IP, revealing the IP and MAC address of connected devices.
Using Wireless Network Watcher (Windows Only)
- Visit http://www.nirsoft.net/utils/wireless_network_watcher.html.
- Click Download Wireless Network Watcher, the second link on the page.
- Run “wnetwatcher_setup.exe” from your Downloads folder and follow the on-screen instructions to install. The program will open upon completion.
- Launch Wireless Network Watcher (eye over router icon). It scans and displays a list of connected devices automatically.
- Press the 'Play' icon in the top-left corner to rescan and update the device list.
- Device Naming and Identification: Each device, when connected, is often recognized by a default name, making it hard to distinguish. By assigning unique, recognizable names, users can swiftly identify unauthorized devices, thereby enhancing network security and immediately addressing unauthorized access to protect their digital assets and personal information efficiently.
Frequent Disconnection
By pinpointing suspicious IP addresses and noting any unsolicited changes to security settings, one can unravel the mystery behind these disruptions and fortify their Wi-Fi against unwelcome intrusions.
- Unknown IP Addresses: Suspicious IP addresses connected to your network need immediate attention. Tracking and identifying these addresses can unveil unauthorized users stealthily utilizing your bandwidth. For instance, an unidentified IP address was found streaming large video files, causing instability and frequent disconnections for the legitimate user.
- Security Setting Changes: Unauthorized users might change security settings to facilitate easier access. Signs include unexpected alteration in the network name, password, or encryption type. A user noticed their Wi-Fi password had been inexplicably changed, blocking their access while an unknown device continued to use the network unabated, highlighting the importance of immediate intervention and correction.
How to Change Router Security Settings
- Update Firmware. Access the router’s management interface by typing 192.168.1.1 or 192.168.0.1 in the browser’s address bar to update its firmware.
- Change Default Login. Navigate to the account or password tab in the router’s management interface to change the default login and password.
- Modify SSID. Access the router’s admin page to change the SSID.
- Implement Strong WiFi Password. Select the appropriate WiFi security type (preferably WPA2 or WPA3 over outdated WEP) and set a robust password. After choosing WPA2 or WPA3, select AES as it’s a secure encryption standard.
- Establish a Guest Network. Create a guest network for visitors and IoT devices to prevent unauthorized access to the main network.
- Disable UPnP and WPS. Alter the protocol status under UPnP to “stealth” to allow network device discovery without exposure to external unauthorized devices.
- Adjust Remote Admin Access. Use an Ethernet cable for secure access to the admin interface.
Methods to Check for Wi-Fi Thieves
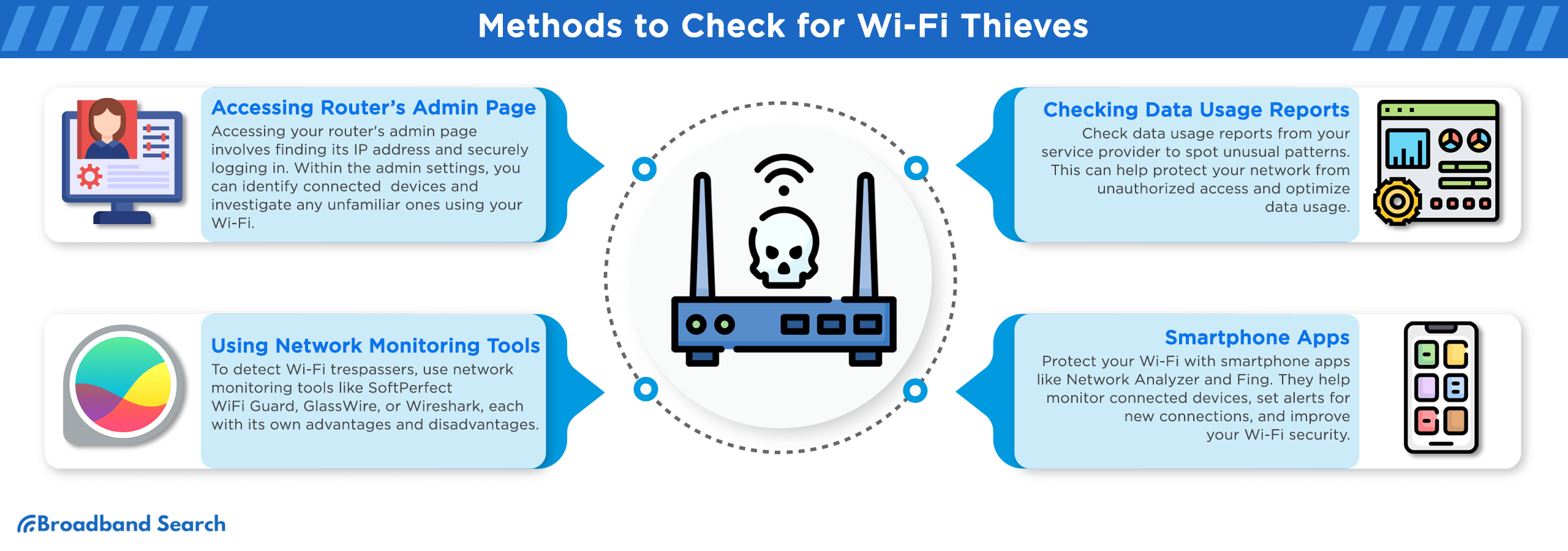
Accessing Router’s Admin Page
Accessing your router's admin page begins with locating its IP address across various operating systems, followed by secure login. Once inside, a careful navigation through the admin settings reveals connected devices, allowing you to spot and investigate unfamiliar entities potentially pilfering your Wi-Fi.
- Finding IP Address: Discovering your local IP address requires slightly more effort compared to identifying your public IP. The method changes based on your device. Here we'll walk you through the steps to locate your local IP on every device.
On Windows
- Press Win + R or click the magnifying glass in the lower left corner.
- Type cmd.
- Enter ipconfig and press Enter in the command line.
- “Default Gateway” shows your local IP; “IPv4 Address” displays the device’s IP.
On MacOS
- Open System Preferences.
- Select Network, then your Wi-Fi or Ethernet connection.
- Click “Advanced” and open the TCP/IP tab.
- “Router” field indicates the local IP; “IPv4 Address” field shows the device’s IP.
On iOS
- Open Settings and navigate to Wi-Fi.
- Tap on your connected Wi-Fi network.
- The “Router” field shows the local IP; “IP Address” field displays the device’s IP.
On Android
- Go to Settings > Connections > Wi-Fi.
- Select your network’s Settings (gear icon).
- Tap “View More” and find your IP address under IPv4 and/or IPv6.
- Logging In and Navigation: Logging into your router’s admin page requires the IP address, usually found on the device's bottom or in the manual. Upon entering this address into a web browser, use the default username and password (often 'admin') to log in. Navigating through this interface, users can explore various settings, including connected devices, security options, and other network parameters.
How to Access Router Admin Settings
Step 1: Find Router’s IP Address
- Routers have unique IP addresses, often 192.168.0.1, 192.168.1.1, or 10.0.0.1. If these aren’t correct, consult the manual, router label, or use command prompt to find the IP.
Step 2: Log in to Router
- Open a browser and enter the router’s IP in the address bar. The router’s login page should appear.
Note on Credentials: Routers usually have default credentials like “admin” for both fields; refer to the manual. For lost custom credentials, consider a factory reset.
Step 3: Explore Router Settings
- Post-login, you’ll access the settings, where layout varies by brand but generally includes 'Network,' 'Wireless,' 'Advanced,' and 'Firewall' settings.
- Network Settings: Adjust IP configuration, subnet mask, and DHCP settings.
- Wireless Settings: Modify Wi-Fi networks, SSID, password, and broadcast channel for optimal signal.
- Advanced Settings: Set up port forwarding, enable Dynamic DNS for remote network access, etc.
- Firewall: Manage network security, toggle firewall, configure VPN and other security settings.
Step 4: Save Changes
- Ensure to save or apply changes made to settings to effectuate them. The button label may vary.
Using Network Monitoring Tools
Utilizing network monitoring tools is an adept strategy to identify Wi-Fi trespassers. These software solutions provide in-depth insights, helping users detect unusual activities, thereby fortifying networks against unauthorized intrusions and safeguarding their digital domains.
- Recommended Tools: SoftPerfect WiFi Guard swiftly spots intruders, providing immediate alerts. GlassWire offers a visual representation of your network activity, highlighting unusual spikes. Meanwhile, Wireshark analyzes network protocols to uncover suspicious behavior, offering an in-depth view into your network's operation, aiding in the swift identification and removal of unauthorized devices.
- Pros and Cons of Each Tool: SoftPerfect WiFi Guard offers user-friendliness and affordability but lacks deep analytics. GlassWire provides extensive visual analytics, though at a higher cost, making it user-friendly but not wallet-friendly for some. Wireshark delivers unparalleled depth in analytics but comes with a steep learning curve, potentially daunting for non-technical users, while providing professional-level insights and control for those able to navigate its complexities.
Checking Data Usage Reports
Understanding these reports from your service provider and recognizing anomalous data patterns are essential steps in safeguarding your network from unauthorized access and ensuring efficient data utilization.
- Accessing Provider Reports: Interpreting reports from your service provider involves accessing your account online and locating the data usage section. These reports typically provide insights into the devices and applications consuming data on your network. For instance, you might notice that a significant portion of your data is being used during late-night hours when your household is usually asleep, raising concerns about unauthorized access.
- Analyzing Data Patterns: Differentiating between normal and suspicious data patterns is crucial. Normal patterns might include increased data consumption during weekends due to streaming or gaming. Conversely, spotting spikes during work hours on weekdays could indicate Wi-Fi thieves exploiting your network for unauthorized activities, such as downloading large files or streaming high-definition content.
Smartphone Apps
Leveraging smartphone apps is an effective strategy in the battle against Wi-Fi thieves. These applications empower users to monitor network activity, set customized alerts, and promptly identify and address unauthorized access, fortifying their Wi-Fi security in the process.
- Network Analyzer, Fing: Network Analyzer scans your Wi-Fi network, listing all connected devices. It provides essential details about each device, helping you identify unauthorized users. For instance, you might spot an unfamiliar smartphone connected to your network. Similar to Network Analyzer, Fing allows you to see all devices on your network, making it easy to pinpoint unauthorized connections. You could receive an alert about a new tablet joining your network, prompting immediate action.
- Setting Alerts: Many Wi-Fi monitoring apps enable you to set up alerts for new device connections. These alerts can help you stay vigilant about potential Wi-Fi thieves. For example, if your child brings a friend over, you can receive a notification when their friend's smartphone connects to your network.
Prevention Techniques
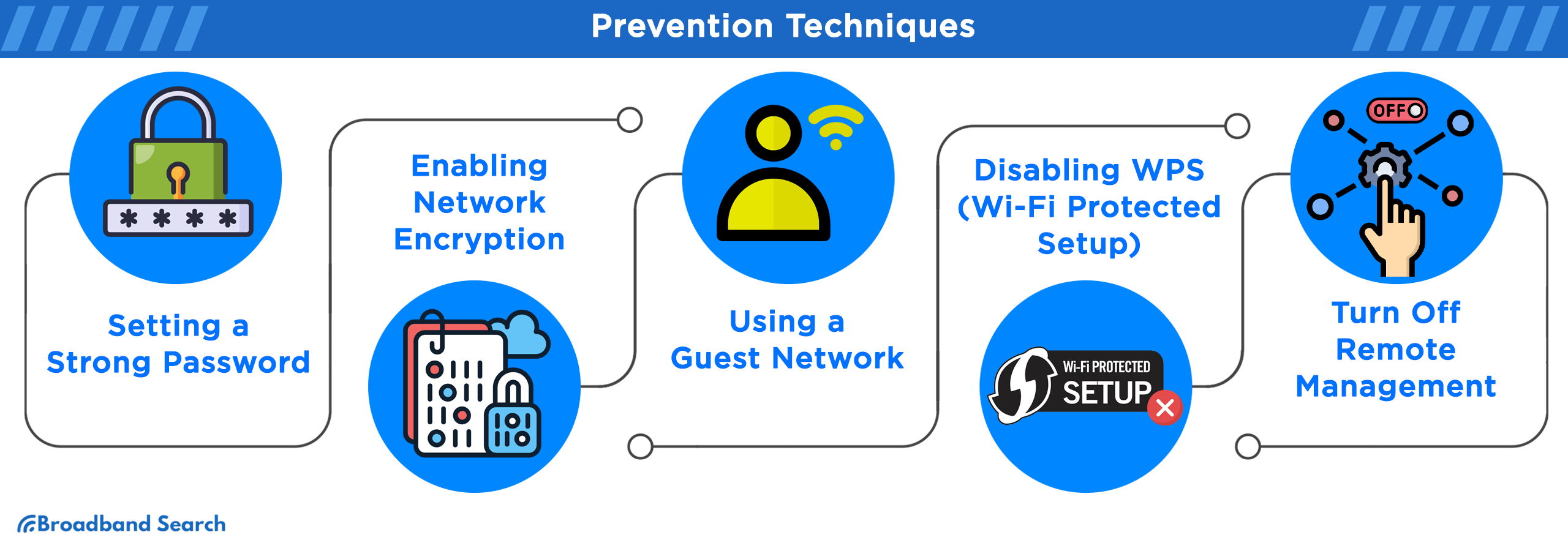
Setting a Strong Password
Setting a strong password is a fundamental pillar of cybersecurity. Crafting a robust password and adhering to a routine of regular updates are critical steps in fortifying your digital defenses, ensuring your online accounts and sensitive information remain secure.
- Creating a Robust Password: Crafting a robust password involves incorporating a diverse mix of upper and lower-case letters, numbers, and symbols. For instance, "P@$$w0rd123" offers complexity and resilience against hacking attempts.
- Updating Password Regularly: Changing your password every 3-6 months is prudent. This precautionary measure ensures that even if your password is compromised, it becomes obsolete before it can be exploited by cybercriminals, enhancing your account's security.
Enabling Network Encryption
Enabling network encryption is a pivotal defense measure in today's digital landscape. The latest WPA3 protocol stands at the forefront of secure networking, encrypting data to shield it from potential interception, ensuring the confidentiality and integrity of your online communications and transactions.
- WPA3 Protocol: The WPA3 protocol is the cutting-edge standard in wireless network security. It employs advanced encryption techniques to fortify your network against potential threats, ensuring that only authorized users gain access. For example, upgrading to WPA3 can prevent unauthorized devices from connecting to your home network, enhancing overall security.
- Importance of Encryption: Encryption is vital as it transforms data into an unreadable format during transmission. For instance, when conducting online banking transactions, encryption ensures that your financial information remains confidential and immune to interception by cybercriminals.
Using a Guest Network
Utilizing a guest network is a robust strategy for enhancing your network's security. Establishing and managing one, along with regulating guest user access levels, is pivotal in safeguarding your primary network while accommodating guests and IoT devices securely.
- Setting Up: Establishing a guest network involves configuring your router to create a separate, secure network for guests. This prevents unauthorized access to your primary network. For instance, if you're hosting a family gathering, you can set up a guest network to provide internet access without exposing your personal devices.
How to Set Up a Guest WiFi Network
Step 1: Access Router’s Web Interface
- Open a web browser on a device connected to your network.
- Enter your router's IP address into the browser's address bar (common ones are 192.168.1.1 or 192.168.0.1).
- Log in using your router’s credentials (default is often "admin" for both username and password).
Step 2: Locate Guest Network Settings
- Once logged in, navigate through the interface to find the “Guest Network” or similar section. This might be located under "Wireless Settings", "Advanced Settings", or a dedicated “Guest Network” tab.
- If you don't see a Guest Network option, your router might not support this feature.
Step 3: Enable & Configure Guest Network
- Enable Guest Network: Turn on or enable the Guest Network feature.
- SSID Setup: Assign a name to your Guest Network; this is the SSID that guests will see when searching for available networks.
- Security Settings: It’s advisable to set up security for the Guest Network, usually WPA2 or WPA3 encryption. Create a secure password for the Guest Network. Share this with guests so they can connect.
- Network Access & Restrictions: Decide if guests can access local network resources (like printers). For added security, it’s best to disable access to local network devices.
- Bandwidth Limit (optional): If available, set a bandwidth limit to prevent guests from slowing down your network.
Step 4: Save & Restart
- After configuring the settings, save or apply the changes.
- Your router might automatically restart, or you may need to do this manually for changes to take effect.
Step 5: Test the Guest Network
- Once the router restarts, use a device to test the Guest Network.
- Check if it appears as an available network and try connecting using the password you set up.
Tips
- Regularly update your router’s firmware to ensure you have the latest security features.
- Change guest network password frequently for enhanced security.
- Limiting Access: Controlling guest user access levels within your network is a pivotal prevention technique. By implementing access restrictions, you can bolster your network's security and protect sensitive data. For instance, you can limit a guest's access to only internet services, preventing them from reaching your private files or connected smart devices, ensuring a safer and more controlled online environment for both you and your guests.
Disabling WPS (Wi-Fi Protected Setup)
Disabling Wi-Fi Protected Setup (WPS) is a crucial security measure as WPS PINs can be vulnerable to hacking. This can be accomplished by accessing your router's admin page, effectively safeguarding your network against potential breaches and unauthorized access attempts.
- Vulnerabilities Explained: Wi-Fi Protected Setup (WPS) can be a security Achilles' heel. Its eight-digit PIN, often printed on routers, can be cracked within hours by determined attackers. For instance, a neighbor with ill intentions could swiftly access your network by exploiting this vulnerability, highlighting the pressing need to disable WPS to fortify your network's defenses and ensure your data's safety.
- How to Disable: Disabling Wi-Fi Protected Setup (WPS) involves logging into your router's admin interface via a web browser. This process typically requires entering the router's IP address and credentials. For instance, when you access your router's admin page, you can navigate to the WPS settings and turn it off, strengthening your network security by eliminating this potential vulnerability.
How to Disable WPS on Netgear Router
- Open a browser; enter www.routerlogin.net in the address bar.
- Log in with username 'admin' and password 'password' (default).
- Navigate to Advanced Setup > Wireless Settings.
- Tick the Disable Router's Pin checkbox under WPS Settings.
- Click Apply.
How to Disable WPS on ASUS Router
- Access 192.168.1.1 in a browser.
- Use 'admin' for both username and password (default).
- Go to Advanced Settings > Wireless.
- Select the WPS tab.
- Toggle the Enable WPS switch to off.
How to Disable WPS on D-Link Router
- Type 192.168.1.1 in a browser’s address bar.
- Log in with 'admin' as username and leave the password field empty (default).
- Click the Setup tab.
- Uncheck the box next to Enable in Wi-Fi Protected Setup.
- Click Save settings.
How to Disable WPS on Linksys
Linksys routers inherently guard against PIN brute-force attacks; thus, WPS cannot be turned off. However, this inbuilt protection makes them resistant to common hacking attempts targeting WPS.
Turn Off Remote Management
Turning off remote management is a fundamental cybersecurity practice that ensures external entities cannot access your router's admin page. This preventive measure is vital for safeguarding your network's security and maintaining control over your network settings.
- Setting it Up: In most cases, you'll locate the option to disable remote management in your router's advanced settings. This crucial step prevents external access to your router's admin page, ensuring that only authorized users within your network can make configuration changes. For instance, a hacker attempting to gain remote access to your router settings will be thwarted by this security measure, bolstering your network's protection.
Below are general steps for various common router brands. Always consider checking the router’s manual or the manufacturer’s website for model-specific instructions.
Netgear
- Access Router Interface: Open a web browser, type www.routerlogin.net or router’s IP.
- Log In: Use your credentials or defaults (usually ‘admin’ for username and ‘password’ for password).
- Navigate: Go to Advanced > Advanced Setup > Remote Management.
- Disable Remote Management: Uncheck the “Turn Remote Management On” box.
- Save: Apply or save changes.
ASUS
- Access Router Interface: Open browser, type router’s IP (often 192.168.1.1).
- Log In: Enter your credentials.
- Navigate: Go to Advanced Settings > System > Administration.
- Disable Remote Management: Locate “Enable Web Access from WAN” and turn it off.
- Save: Apply or save changes.
TP-Link
- Access Router Interface: Open browser, type router’s IP (commonly 192.168.0.1 or 192.168.1.1).
- Log In: Enter login details.
- Navigate: Go to Advanced > System Tools > Administration.
- Disable Remote Management: Find and disable “Remote Management.”
- Save: Save or apply changes.
D-Link
- Access Router Interface: Open a browser, type router’s IP.
- Log In: Enter login information.
- Navigate: Go to Settings > Management.
- Disable Remote Management: Uncheck “Enable Remote Management” or similar option.
- Save: Save settings or reboot router if necessary.
Linksys
- Access Router Interface: Open browser, enter router’s IP (often 192.168.1.1).
- Log In: Enter credentials.
- Navigate: Go to Administration > Remote Management.
- Disable Remote Management: Set “Remote Management” to Disable.
- Save: Save settings.
Google Nest WiFi
Google Nest WiFi routers are controlled through the Google Home app, and they don't traditionally offer an option to disable remote management as it's tied to your Google account. Ensure your Google account has a strong password and two-factor authentication enabled for security.
Immediate Action Steps if Wi-Fi is Compromised
Changing Wi-Fi Password
Changing your Wi-Fi password is a crucial immediate action step if you suspect your network has been compromised. It's a swift and effective measure to thwart unauthorized access and restore your network's security.
- Step-by-Step Guide: A step-by-step guide for your specific router brand can help swiftly navigate the process. This immediate action ensures that unauthorized access is revoked, reinforcing your network's security and safeguarding your data from potential threats. It's a vital step in reclaiming control over your network and maintaining a safe online environment.
How to Change NETGEAR Router WiFi Password
- Open a web browser on a device connected to the NETGEAR router.
- Visit www.routerlogin.net. A login prompt will appear.
- Input your username and password. By default, the username is 'admin'. The initial password is the one you set during your first login. Both are case-sensitive.
- You'll be directed to the BASIC Home page or Dashboard.
- Click on "Wireless." For Nighthawk Pro Gaming routers, choose Settings > Wireless Setup.
- Type in your desired network name in the "Name (SSID)" field.
- Input your new password in the "Password (Network Key)" fields.
- Click "Apply" to save the changes.
If your device gets disconnected after the changes, search for available Wi-Fi networks and reconnect using the updated password.
How to Change ASUS Router WiFi Password
- Start by logging into your ASUS router to access the web-based dashboard where you can adjust Wireless settings.
- Navigate to Wireless Settings. Click on "Wireless" in the left navigation panel. Under the "General" tab, locate the "Pre-shared key" field.
- Enter your new, secure password in the "Pre-shared key" field. Consider creating a random and robust password or utilizing a password manager like 1Password for enhanced security.
- After saving the changes, test the newly set Wi-Fi password by connecting a wireless device to the network.
How to Change D-Link Router WiFi Password
- Launch an Internet browser and type in http://dlinkrouter.local or http://192.168.0.1 in the address bar.
- Input the Admin account password. If it's unchanged from the default, leave it blank. Press Log In. Typically, the default username is 'admin', and the password is either 'admin' or left blank.
- Navigate to Wireless Settings through the dropdown menus.
- Enter a new password in the Password field for the desired wireless band. You'll need this new password to connect devices to your wireless network, which might necessitate updating the configurations on your wireless devices.
- Click Save to apply the changes.
How to Change TP-Link Router WiFi Password
- Use a browser to log in to the router’s admin panel through its default IP address, which is either 192.168.0.1 or 192.168.1.1.
- Input the default credentials, usually both username and password are 'admin'.
- Go to Wireless > Wireless Security > WPA/WPA2 - Personal (Recommended) > Password.
- Type in your desired password and save the changes.
How to Change Linksys Router WiFi Password
- Type 192.168.1.1 in your web browser's address bar.
- On the Splash page, click Continue to Linksys Smart Wi-Fi.
- Click Reset Password.
- Input your Recovery Key, located on the bottom of your router. Avoid unplugging any cables from the router during this process.
- Create and enter a new password; optionally, you can also provide a password hint.
- Click Reset. Your password is now updated.
- Ensuring Password Strength: Utilize password generators like LastPass to create complex and unique passwords. Password managers such as 1Password help store and manage them securely. Tools like Gibson Research Corporation's Password Haystacks gauge password strength, offering guidance on crafting robust passwords.
Updating Firmware
Updating your Wi-Fi router's firmware is an immediate action to reclaim security. Discovering and installing these updates can be vital. By following safe installation practices and ensuring your router's firmware is up-to-date, you can effectively fortify your network and protect against potential vulnerabilities.
- Locating Updates: Manufacturers typically provide firmware updates on their official websites, often under the "Support" or "Downloads" section. Identify your router's model and serial number, and download the latest firmware version applicable to your device. Installing these updates ensures you have the latest security patches and enhancements, bolstering your network's defenses against potential threats.
Netgear
- Open a browser, go to routerlogin.net or router’s IP, and log in.
- Click on Advanced > Administration > Firmware Update or Router Update.
- Click Check, and if an update is available, follow the prompts to install.
ASUS
- Enter router’s IP (usually 192.168.1.1) in a browser and log in.
- Go to Administration > Firmware Upgrade.
- Click on Check for the latest firmware version, then download and install if available.
TP-Link
- Enter router’s IP (commonly 192.168.0.1 or 192.168.1.1) in a browser and log in.
- Go to Advanced > System Tools > Firmware Upgrade.
- Click on Check for upgrade, download, and install if available.
D-Link
- Open a browser, type in the router’s IP (commonly 192.168.0.1), and log in.
- Go to Tools > Firmware.
- Visit D-Link’s official website, find your router model, download the latest firmware, and upload it through the router interface.
Linksys
- Open a browser, type in the router's IP (often 192.168.1.1), and log in.
- Go to Connectivity > Basic.
- Click Check for Updates, then Download and install if any are available.
Google Nest WiFi
Use Google Home App: Firmware updates are automatic; you can check the status and firmware version using the Google Home App.
- Safe Installation Practices: When updating your Wi-Fi router's firmware, adhere to these best practices to avoid installation errors:
- Backup Settings: Before updating, back up your router's settings to restore them if needed.
- Use Manufacturer's Website: Download firmware updates only from the manufacturer's official website to ensure authenticity.
- Read Release Notes: Review release notes to understand what the update addresses and its potential impact.
- Stable Connection: Ensure a stable power source and network connection to prevent interruptions during the update.
- Follow Instructions: Carefully follow the manufacturer's instructions for installation.
- Monitor Progress: Keep an eye on the update's progress, and do not interrupt it until completed.
By following these safe installation practices, you can ensure a successful firmware update, strengthening your network's security and guarding against potential vulnerabilities effectively.
Blocking Unauthorized Devices
Blocking unauthorized devices from your Wi-Fi network is a swift and essential response to a security breach. This proactive measure involves accessing your device block list and adding intruding devices to ensure the security and integrity of your network.
- Accessing Device Block List: After investing in home or work Wi-Fi, it’s essential to optimize the return on your investment. Unauthorized access to your network not only leads to significant drops in network speeds but also risks unauthorized access to private data. Sometimes, even willingly sharing your Wi-Fi password with friends and family can result in reduced speeds.
How To Remove Devices From WiFi Router
- Open a web browser and enter your router’s IP address (commonly 192.168.1.1 or 192.168.0.1). Log in with your credentials (if you haven’t changed them, the default is often admin for both username and password).
- Look for a section called “Device List,” “Connected Devices,” “Wireless,” or something similar. This section lists all devices connected to your Wi-Fi network. Each device is usually identified by its name, MAC address, and assigned IP address.
- There might be an option to disconnect or remove devices directly. If not, you can block access by adding the device’s MAC address to a “MAC filter” or “Access Control” list and set it to “deny” or “block.”
- For immediate disconnection of all unauthorized devices, change your Wi-Fi password. Navigate to the “Wireless” or “Wireless Security” section and change the password.
- Save your changes and restart your router if necessary to apply the settings.
- Adding Devices to Block List: Effectively managing a block list for your network involves adding devices to this list to prevent unauthorized access. Here’s a step-by-step guide on how to add devices to your block list and manage it efficiently
How to Block a Device From My Wifi Router
- Access Router Settings :Open a browser and enter your router’s IP address (commonly 192.168.1.1 or 192.168.0.1). Log in using your credentials.
- Locate MAC Address Filtering or Access Control: Find the section called "MAC Address Filtering," "Access Control," or something similar. This could be under “Wireless,” “Security,” or “Advanced” settings, depending on your router model.
- Add Devices to the Block List: Find Unauthorized Devices, look for the list of devices connected to your network. Identify the ones you don’t recognize or want to block. Add to Block List, enter or select the MAC address of the device you want to block and add it to the block list. Ensure to enable the block or deny option for the added devices.
- Apply and Save Settings: After adding devices to the block list, save or apply the changes.
- Restart Your Router (if necessary): Some routers might require a restart for changes to take effect.
Performing a Factory Reset
If your network isn’t performing well, such as web pages not loading, Netflix freezing, or smart speakers not playing music, restart your router and modem. This allows the devices to cool and their memory to clear.
- Unplug Router, Modem, Managed Hardware: Unplug the router, modem, and any managed network hardware. Leave unmanaged devices powered unless you suspect they’re causing issues.
- Wait 30 Seconds: This cooling-off period lets your ISP and connected devices know the router and modem are offline. Do this step even if you're unsure of the specific connection issue.
- Power on Modem: Plug in and power on the modem, which connects to your internet service.
- Wait 60 Seconds: This allows the modem to authenticate with your ISP and obtain a public IP address.
- Power on Router: Plug in and power on the router, which is usually located next to the modem. Skip this step for combination modem-routers, as they initialize automatically.
- Wait 2 Minutes: This allows the router and connected devices to boot and obtain IP addresses from the router’s DHCP service. If you powered down other network hardware, turn it back on starting from the outermost device and moving inward.
- Test Network: After restarting, check if the network issues are resolved.
- Engage Professional Support: If you're unsure about performing a factory reset or need assistance with complex network configurations, it's advisable to seek professional support. For instance, if your network is compromised due to advanced cyberattacks, a professional can assess the damage and implement security measures effectively. You can find professional support from reputable IT service providers or network security experts. These professionals possess the knowledge and expertise needed to restore your network's security and integrity after a compromise, ensuring a swift and effective resolution.
Advanced Security Measures
Setting up MAC Address Filtering
Setting up MAC Address Filtering is an advanced security measure that enhances network protection. Each device has a unique MAC address, and by configuring your router settings to allow only known MAC addresses, you establish an additional layer of security to safeguard your network from unauthorized access.
- Explanation of MAC Address: A MAC address (Media Access Control address) serves as a unique identifier for every network-enabled device. This address is embedded in the device's network hardware, allowing network routers to recognize and differentiate devices. For example, a MAC address resembles "00:1A:2B:3C:4D:5E," and it distinguishes devices like smartphones, laptops, and smart TVs, enabling precise identification within a network for enhanced security measures such as MAC address filtering.
- Guide to Enabling Filtering: Enabling MAC address filtering is a potent security measure accessible through your router's settings. By configuring this feature, you can exclusively permit known MAC addresses to connect to your network, denying access to any unlisted devices.
How to Enable MAC Address Filtering
- Open a web browser, enter your router's IP address in the address bar to access the admin site. Refer to the manual or manufacturer’s website for the specific IP (common ones include "192.168.1.1," "192.168.0.1," "10.0.0.1").
- Use the admin username and password to log in. If unset, use the default credentials found on the router, manual, or manufacturer’s site (often "admin", "password", "12345", or left blank).
- Navigate to the MAC Filtering option in the interface. Its location and name vary—possible names include "MAC Filter", "Network Filter", "Access Control", found under "Wireless", "Security", or "Advanced". Consult the manual or support site if needed.
- Once in MAC Filtering, select to add a new MAC address, usually by clicking "Add", a plus sign (+), or similar.
- Input the unique MAC address of the device you want to filter. Find it on your device's "About" or "Settings" section. A MAC address typically looks like "08:00:27:0E:25:B8".
- After adding the MAC address, save or apply changes. You can add multiple addresses if necessary.
- Activate MAC Filtering with the relevant option, often labeled "Enable MAC Filtering", "MAC Restrict Mode", or similar, and select "On" or "Enable". A router reboot may be required to apply changes.
Investing in Quality Hardware
Investing in quality hardware is a paramount advanced security measure. This includes scrutinizing the best routers for security, conducting reviews, and making comparisons. Additionally, emphasizing the significance of regular hardware updates, addressing why and how often they should occur, is essential.
- Best Routers for Security: When it comes to routers, choosing models with robust security features is crucial. Look for routers from reputable manufacturers known for prioritizing security in their devices. Features like WPA3 encryption, automatic firmware updates, and strong firewall capabilities can significantly enhance your network's protection against cyber threats, making them essential considerations when selecting a router for your network.
- Importance of Regular Hardware Updates: Hardware updates often include security patches that address vulnerabilities. The frequency of updates depends on the manufacturer, but it's advisable to check for updates at least every few months. By keeping your hardware up-to-date, you ensure that your network remains protected against emerging threats, safeguarding your data and digital environment effectively.
- Enhanced Security: Up-to-date hardware often includes the latest security features, protecting your network from evolving threats.
- Performance Optimization: Newer hardware can handle increasing network demands, ensuring smoother and more efficient operations.
- Future-Proofing: Investing in quality hardware ensures compatibility with emerging technologies, extending the lifespan of your network equipment and reducing the need for frequent replacements.
VPN for Extra Layer of Security
Adding a VPN (Virtual Private Network) to your security arsenal is an advanced measure for bolstering protection. This extra layer of security encrypts your internet connection, shielding sensitive data from prying eyes and ensuring online privacy.
- Benefits of VPN: The surge in cybercrime has made online surfing increasingly precarious for users in India, exposing them to risks like hacking and theft of private information. According to the most recent data from the National Crime Record Bureau, India experienced a 63.5% increase in reported cybercrime cases in 2019 alone. These cases encompass financial hijacking and email account takeovers leading to ransom demands. To safeguard their precious data, online users should implement robust safety measures. Opting for a dependable VPN service is a prime strategy for enhancing online security.
- Privacy: A VPN encrypts your internet traffic, making it nearly impossible for anyone to intercept or monitor your online activities. This ensures your data remains confidential and protected.
- Security: VPNs establish a secure tunnel between your device and the internet, safeguarding against cyber threats and ensuring your online presence remains safe from hackers and malicious actors.
- Performance: Some VPNs can enhance performance by bypassing geographical restrictions, enabling faster access to region-restricted content, and reducing the risk of network congestion.
- Best VPN Services: Opting for a top-tier VPN service ensures that your data remains encrypted and secure while traversing the internet. Features like strong encryption protocols, a wide server network, and a strict no-logs policy are crucial when choosing the best VPN service for enhanced security. Thoroughly researching and selecting a reputable VPN provider guarantees that your online activities remain private and protected.
- NordVPN: With NordVPN, you gain access to a vast server network, top-grade encryption, and a strict no-logs policy, ensuring unparalleled privacy, security, and the ability to bypass geo-restrictions.
- ExpressVPN: ExpressVPN offers high-speed servers in numerous locations, strong encryption, and exceptional customer support. It provides the fastest and most secure browsing experience while maintaining your online anonymity.
- CyberGhost: CyberGhost excels with user-friendly apps, robust privacy features, and dedicated streaming servers. It's an ideal choice for hassle-free, secure, and unrestricted access to online content and services.
Utilizing Advanced Firewall Settings
Firewalls serve as digital barriers, safeguarding your network from malicious threats and unauthorized access. This advanced security measure allows you to tailor your firewall configurations to suit your specific needs, ensuring that your digital environment remains fortified against evolving cyber threats.
- Configuring Advanced Firewall settings: By activating and optimizing these settings, you can tailor your firewall to suit your specific needs. This involves configuring rules, filtering traffic, and monitoring network activity. With advanced firewall protection in place, you fortify your network's defenses, ensuring that only trusted traffic enters while keeping cyber threats at bay.
How to Enable Advanced Firewall Protection
- Open a web browser. Enter your router's IP address in the address bar. Common addresses are 192.168.1.1, 192.168.0.1, or 10.0.0.1. Log in using your username and password.
- Navigate to the firewall section. This might be under “Advanced,” “Security,” or a similar tab.
- Look for “Advanced Firewall,” “Firewall Protection,” or similar. Enable the feature. There might be a toggle, checkbox, or drop-down menu where you can select ‘Enabled’ or ‘On’.
- Configure Advanced Settings: Set Security Level: Choose a security level. ‘High’ is more secure but may block some legitimate traffic. ‘Low’ or ‘Medium’ may be more appropriate for general use. Enable SPI (Stateful Packet Inspection), this feature scrutinizes incoming data packets more thoroughly. Create Rules, set rules for inbound and outbound traffic. Specify which types of traffic are allowed or blocked.
- Enable content filtering and add websites or keywords you want to block or allow.
- Once you’ve made your selections, save or apply the changes.
- Test the firewall to ensure it’s working as expected. You can use online tools or attempt to access the content you’ve blocked.
- Regularly check for firmware updates for your router and monitor the firewall logs, if available.
- Implementing Network Segmentation: An IBM report highlighted that the average total cost of data breaches surged to $4.24 million USD from $3.86 million—the steepest in 17 years. With these escalating costs and the growth of remote work, cybersecurity has emerged as a paramount concern for businesses in 2021. Consequently, network segmentation is now a central approach for entities aiming to fortify intricate networks.
7 Best Practices for Network Segmentation & Segregation
- Implement Least Privilege: Grant access based solely on necessity, limiting exposure within and across systems. Use least privilege principles and role-based access to restrict access, facilitating easier network traffic monitoring and enhancing security.
- Restrict Third-party Access: Minimize entry points by limiting third-party access, addressing a major vulnerability. Recent data reveals 74% of breached organizations had overly generous third-party privileges. Establish isolated portals for necessary third-party access, confining them to essential areas.
- Facilitate Legitimate Access: Design your network to make legitimate access simpler than illicit entry. Ensure secure user access points and consider potential illegitimate access routes to reinforce security.
- Audit & Monitor Regularly: Continuous network monitoring and auditing are crucial following initial segmentation. Regular assessments, especially during business changes, help identify architectural gaps and adjust segmentation for optimal security and performance.
- Avoid Over-segmentation: Gartner warns against excessive segmentation, which complicates management and increases costs. While it’s essential to group like resources, avoid overly granular segmentation, focusing instead on broader, necessary divisions.
- Group Similar Resources: Consolidate similar network resources into single databases to efficiently apply security policies and streamline management.
- Visualize Your Network: Understanding your network’s composition and user needs is vital for effective segmentation. Create a network diagram for an overview, helping to plan and implement successful, secure network architecture.
The Bottomline
In this exploration of advanced security measures, we've delved into the essential strategies and tools that fortify your digital environment. From VPNs and MAC address filtering to advanced firewall settings, each component contributes to a multi-layered defense system that safeguards your network against a constantly evolving landscape of cyber threats.
It's imperative to emphasize the paramount importance of Wi-Fi security. As our lives become increasingly interconnected and reliant on digital technologies, protecting our Wi-Fi networks is not just a matter of convenience but a fundamental aspect of personal and business security. Data breaches, cyberattacks, and unauthorized access can have severe repercussions, making it our collective responsibility to take proactive measures in securing our digital realms.
As we conclude, we urge you to take action. Implement the advanced security measures discussed, regularly update your network infrastructure, and stay informed about emerging threats. By doing so, you not only protect your data and privacy but also contribute to a safer digital ecosystem for us all. Your proactive stance in Wi-Fi protection can make a substantial difference in the face of ever-evolving cyber challenges.
FAQ
How often should I check for unauthorized Wi-Fi users?
Regular monitoring is essential. Conduct weekly checks for unauthorized users as a baseline. During high-risk periods, like when cyber-attacks surge, increase the frequency of checks to ensure optimal network security.
What should I do if my Wi-Fi is repeatedly compromised?
Implement stronger security protocols, like WPA3 encryption, and consistently change your Wi-Fi password. Consider professional cybersecurity consultation for a robust assessment and solution if breaches persist, to protect sensitive data effectively.
Do I need advanced technical knowledge to secure my Wi-Fi?
Advanced technical knowledge isn't mandatory but helpful. Basic security measures, including strong passwords, network encryption, and firewall utilization, provide substantial protection. For advanced security, consider professional services or comprehensive self-learning to enhance your technical proficiency.
What are the risks associated with unauthorized Wi-Fi access?
Unauthorized access exposes your network to various risks including data theft, illegal content download, and network performance degradation. It may also compromise connected devices, leading to potential financial loss and privacy breaches.
What are the risks associated with unauthorized Wi-Fi access?
Risks include exposure to malware, potential data breaches, and identity theft. Unauthorized users might also engage in illegal activities using your network, implicating you unintentionally. It’s crucial to secure your Wi-Fi to avoid these hazards.